
In this article - detailed information on which methods can be used to hack custom passwords and why you are vulnerable to such attacks. And at the end you will find a list of online services that will allow you to find out whether your password has already been compromised. There will also be (already there) the second article on the topic, but I recommend reading reading from the current review, and then go to the next one.
Update: Ready The following material is the security of passwords, which describes how to maximize their accounts and passwords to them.
What methods are used to hack passwords
Password cracking is not used much of a wide range of different techniques. Almost all of them are known and almost any compromise of confidential information is achieved through the use of individual methods or combinations thereof.Phishing
The most common way to which today is "leading" passwords of popular postal services and social networks is phishing, and this method works for a very large percentage of users.
The essence of the method is that you fall on, as you think, a familiar site (the same Gmail, VC or classmates, for example), and for one reason or another, you are asked to enter your username and password (for the entry, confirmation of something, For his shift, etc.). Immediately after entering the password turns out to be at intruders.
How this happens: You can receive a letter, allegedly from the support service, which is reported on the need to enter the account and the link is given, when you go to which the site opens, exactly copied original. An option is possible when after a random installation of undesirable software on a computer, the system settings are changed in such a way that when you enter the address browser in the address bar, you actually fall on the phishing site in exactly the same way.
As I noted, very many users come across this, and usually it is associated with inattention:
- Upon receipt of the letter, which in one form or another offers you access your account on a particular website, pay attention to whether it was actually sent to the mail address on this site: commonly used similar addresses. For example, instead of [email protected], may be [email protected] or something similar. However, the correct address does not always guarantee that everything is in order.
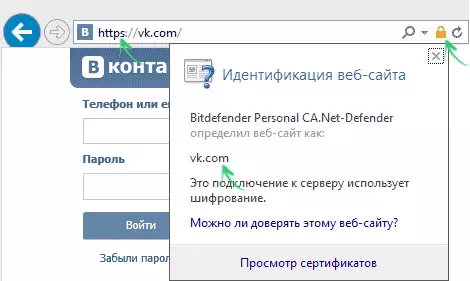
- Before you enter your password, look carefully in the address bar of the browser. First of all, it should be specified that the site you want to go. However, in the case of malicious software on a computer that is not enough. It should also be paid to the presence of a connection encryption that can be determined using the HTTPS protocol instead of HTTP and the image of the "lock" in the address bar, by clicking on which, you can make sure that you are on this site. Almost all serious resources requiring login to use encryption.
By the way, I note that the phishing attacks and methods of password generation (described below) do not mean today the painstaking vigorous work of one person (that is, he does not need to introduce a million passwords by hand) - all make special programs, quickly and in large volumes And then report on the success of the attacker. Moreover, these programs can not work on a hacker's computer, and hidden on your and thousands of other users, which at times increases the effectiveness of hacking.
Selection of passwords
Attacks using password selection (Brute Force, rude strength in Russian) is also sufficiently common. If a few years ago, most of these attacks were really busting of all combinations of a certain set of characters to compile passwords of a certain length, then at the moment everything is somewhat simpler (for hackers).The analysis of the populats leaked in recent years in recent years shows that less than half of them are unique, while on those sites where "live" predominantly inexperienced users, the percentage is completely small.
What does this mean? In general, the fact that hacker does not need to sort out non-regular millions of combinations: having a base of 10-15 million passwords (approximate number, but close to truth) and substituting only these combinations, it can hack almost half of the accounts on any site.
In the case of a focused attack on a specific account, in addition to the database, simple bust can be used, and modern software allows you to do it relatively quickly: the password of 8 characters can be hacked in a matter of days (and if these characters are a date or a combination of name and dates that are not uncommon - in minutes).
Note: If you are using the same password for various sites and services, as soon as your password and the corresponding email address will be compromised on any of them, using the Special For the same combination of login and password, it will be tested on hundreds of other sites. For example, immediately after leakage of several million passwords Gmail and Yandex at the end of last year, the wave of hacking of Origin accounts, Steam, Battle.net and Uplay (I think, and many others, simply appealed to me with the specified gaming services).
Hacking sites and receiving hash passwords
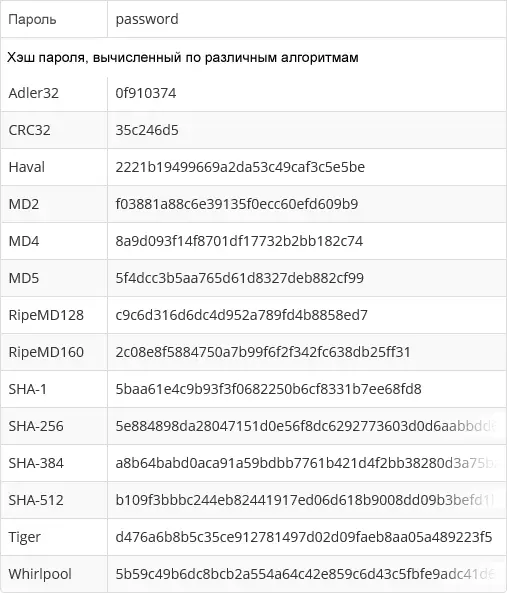
Most of the serious sites do not store your password in the form in which you know it. Only hash is stored in the database - the result of applying an irreversible function (that is, from this result cannot be obtained from your password again) to the password. At your entrance to the site, the hash is re-calculated and, if it coincides with what is stored in the database, then you have entered the password correctly.
As it is easy to guess, it is hashi, and not the passwords themselves just for security reasons - so that with a potential hacking and receipt of the database attacker, he could not use the information and find out the passwords.
However, quite often, to do it it can:
- To calculate the hash, certain algorithms are used, mostly known and common (i.e. everyone can use them).
- Having bases with millions of passwords (from the point about the bust), the attacker also has access to the hash of these passwords calculated by all accessible algorithms.
- Mapping information from the received database and hashing passwords from its own base, you can determine which algorithm is used and recognized real passwords for part of the entries in the database by simple comparison (for all undesiotic). And the means of extinguishing will help you find out the rest of the unique, but short passwords.
As you can see, marketing allegations of various services that they do not store your passwords on their website, do not necessarily protect you from his leakage.
Spyware SPYWARE
Spyware or spyware - a wide range of malicious software that is hiddenly installed on a computer (also spy functions can be included in some kind of necessary software) and collecting information about the user.Among other things, individual types of Spyware, for example, keyloggers (programs that track the keys you click) or hidden traffic analyzers can be used (and used) to obtain custom passwords.
Social engineering and questions for password recovery
According to Wikipedia, social engineering is telling us - the method of access to information based on the peculiarities of the psychology of a person (here can be attributed and mentioned above phishing). On the Internet you can find many examples of using social engineering (I recommend searching and read - it is interesting), some of whom are striking with their elegance. In general terms, the method is reduced to the fact that almost any information needed to access confidential information can be obtained using human weakness.
And I will give only a simple and not particularly elegant household example related to passwords. As you know, on many sites to restore the password, it is enough to introduce an answer to the test question: at what school did you study, the maiden name of the mother, the nickname of a pet ... Even if you have no longer placed this information in open access on social networks, as you think it is difficult Will with the help of the same social networks, being familiar with you, or specially becoming acquainted, unobtrusively get such information?
How to find out what your password was hacked
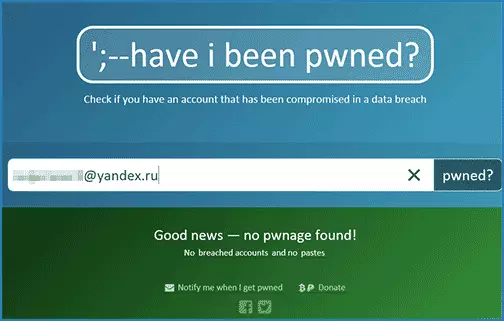
Well, at the end of the article, several services that allow you to find out if your password has been hacked by reconciling your email address or username with password databases that have been in hacker access. (I surprise me slightly that among them too much percentage of databases from Russian-speaking services).
- https://haveibeenpwned.com/
- https://breachalarm.com/
- https://pwnedlist.com/query.
Have you discovered your account in the list of famous hackers? It makes sense to change the password, but in more detail about safe practices in relation to account passwords I will write in the coming days.
