
As you know, the owners of personal computers use the system for storing any data, whether something personal or working. That is why the overwhelming majority of people may be interested in the subject of data encryption, which implies setting some restrictions on access to files from unauthorized persons.
Further, in the course of the article, we will reveal the main features of data coding, as well as tell about special purpose programs.
Encryption data on a computer
First of all, such a detail is worthy as the relative simplicity of the process of protecting data on a computer running various operating systems. Mainly this applies to inexperienced users whose actions could entail consequences in the form of loss of access to data.
Encryption itself is a hide or movement of important data into the zone, inaccessible to other people. Typically, for these purposes, a special folder with a password that performs the role of temporary or permanent storage is created.
Adhere to the recommendations to subsequently avoid access to access.
As it is easy to guess, the TPM hardware module has its own partition with parameters in the Windows operating system.
- Open the Windows Search Window using the "Win + R" key.
- In the "Open" text graph, insert a special command and click on the "OK" button.
- In the control window of the Trusted Platform Module (TPM), you can get a brief information about its work.
TPM.MSC.
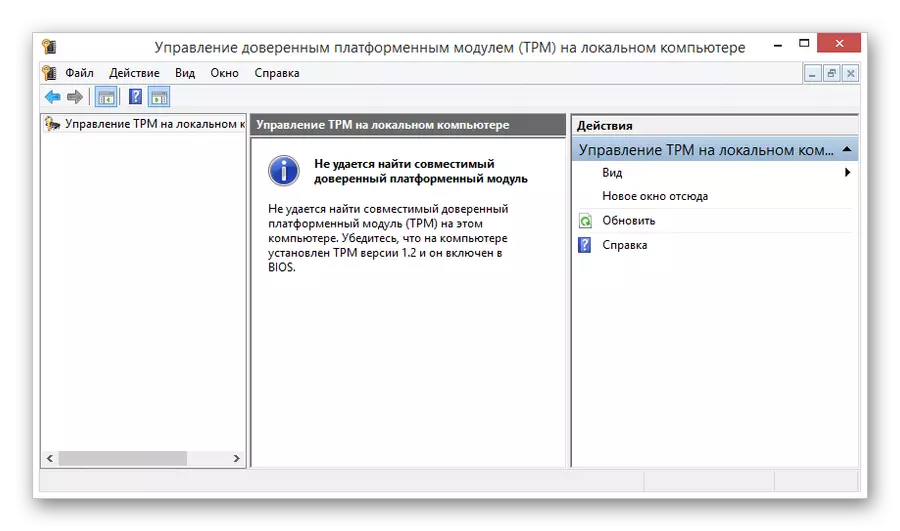
If the specified error you have not been seen, you can skip the following instructions for the settings, moving directly to the encryption process.
To get rid of the specified error, you must perform a number of additional actions associated with changing the local group policy of the computer. Immediately note that in the event of any unforeseen and not affected by us, you can roll back the system to an early state, using the functional "Restoration of the system".

If everything was done correctly, you will find yourself in the "Local Group Policy Editor" window.
- In the main list of folders in the Computer Configuration unit, deploy the child section "Administrative Templates".
- In the following list, expand the "Windows components" directory.
- From a rather extensive list of folders in the disclosed section, find the "This policy parameter allows you to select BitLocker disk encryption."
- Next, you need to select the "Operating System disks" folder.
- In the main workspace, located on the right side of the block with the folder catalog, switch the viewing mode to the "standard".
- In the documents submitted list, find and open the optional authentication section when starting.
- You can open the edit window as a double click LKM, and through the "Change" item in the PCM menu.
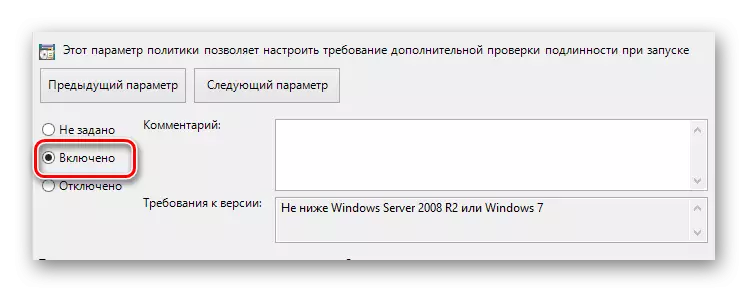
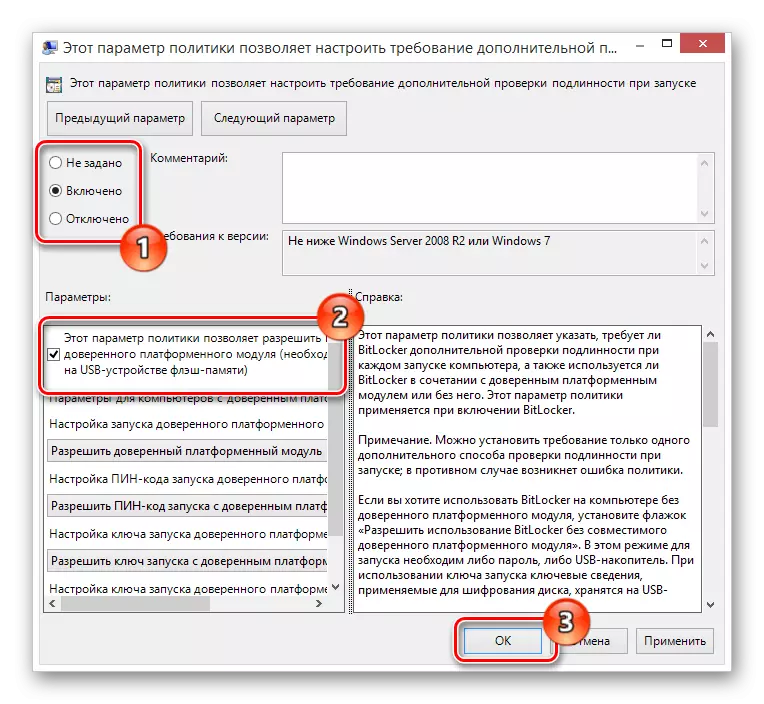
- At the top of the open window, find the parameter control unit and set the allocation opposite the option "Included".
- To further avoid possible complications, be sure to check the presence of a check mark in the "Parameters" window next to the paragraph specified in the screenshot.
- After completing the setting of recommended values for Group Policy Settings, use the "OK" button at the bottom of the working window.

This will allow you to search and edit the desired parameters with a slightly large convenience.



Having done everything in accordance with our prescriptions, you will no longer encounter an error of the TPM platform module.
In order for the changes to enter into force, no reboot is required. However, if something went wrong with you, I had to restart the system.
Now, having understood with all the preparatory nuances, you can go directly to the protection of data on the disk.
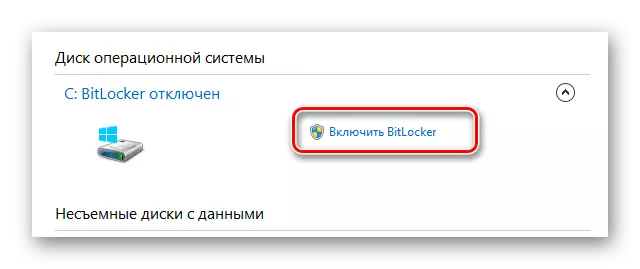
- Go to the data encryption window in accordance with the first instruction in this method.
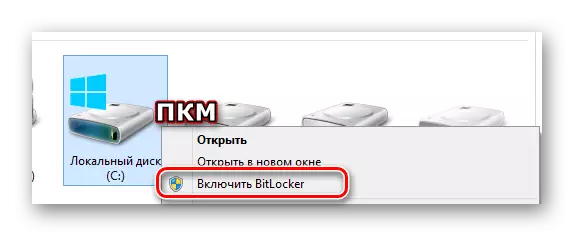
- The desired window can also be opened from the system partition "My Computer" by clicking on the right disk with the right mouse button and selecting the "Enable BitLocker" item.
- After successfully initializing the encryption process, the bitchker will automatically check the compatibility of the configuration of your computer.
In the subsequent stage, you will need to select one of two encryption options.
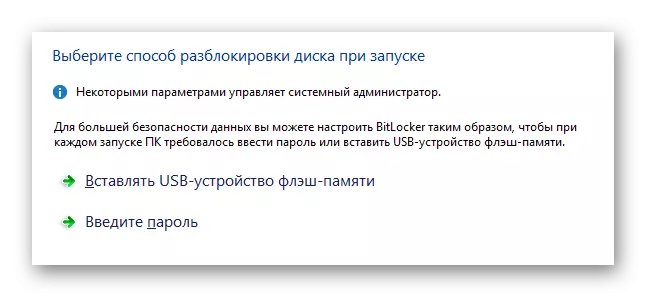
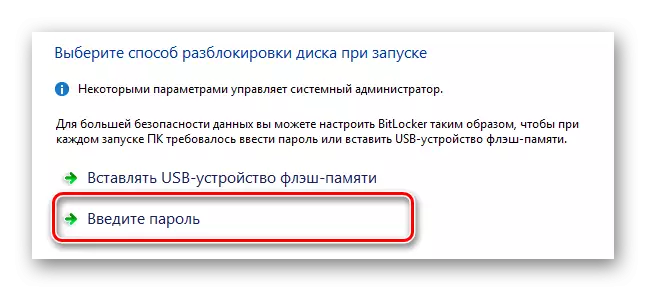
- Optionally, you can create a password for subsequent access to information.
- In the case of a password, you will need to enter any convenient set of characters in full compliance with the requirements of the system and click on the "Next" key.
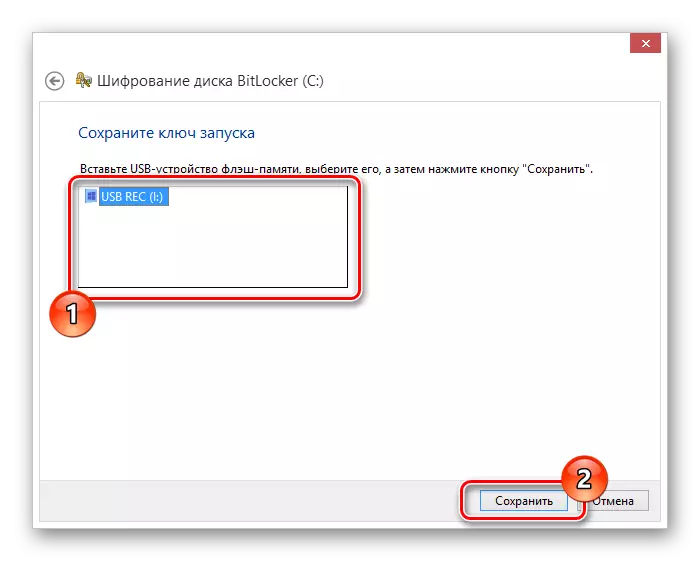
- If you have a good USB drive, select "Insert USB Flash Memory Device.
- In the list of available drives, select the desired device and use the "Save" button.

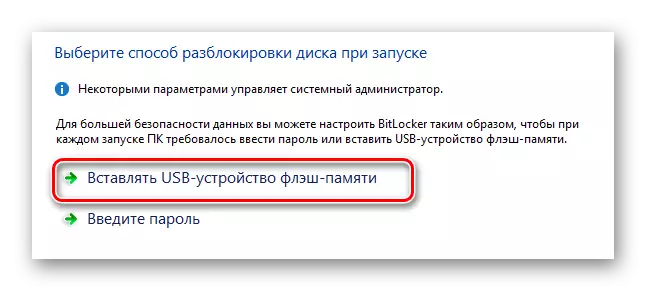
Do not forget to connect your USB device to PC.
Whatever encryption method has been selected, you will find yourself on the key creation page with the key.
- Specify the most acceptable type of archive for you for storing the access key and click on the Next button.
- Select the data encryption method on the disk, guided by the presented Bitokher Recommendations.
- In the last step, set the box "Run the BitLocker scan" and use the "Continue" button.
- Now in a special window, click the "Restart Now" key, do not forget to insert a flash drive with the encryption key.
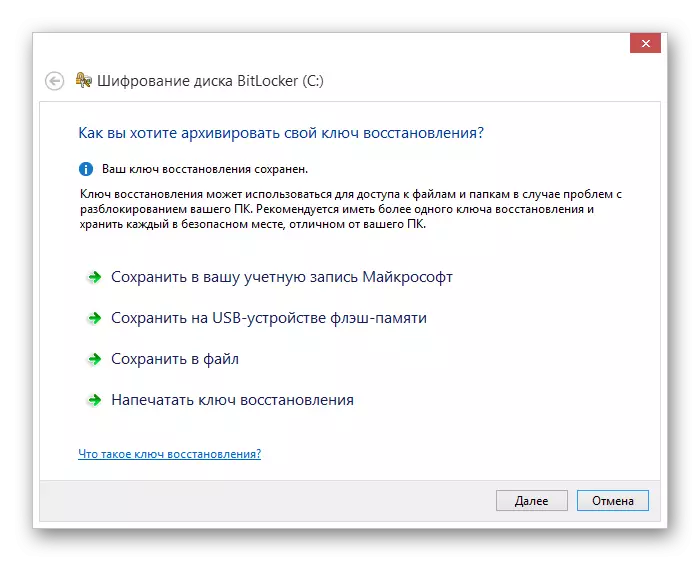
We use the key to save on the flash drive.
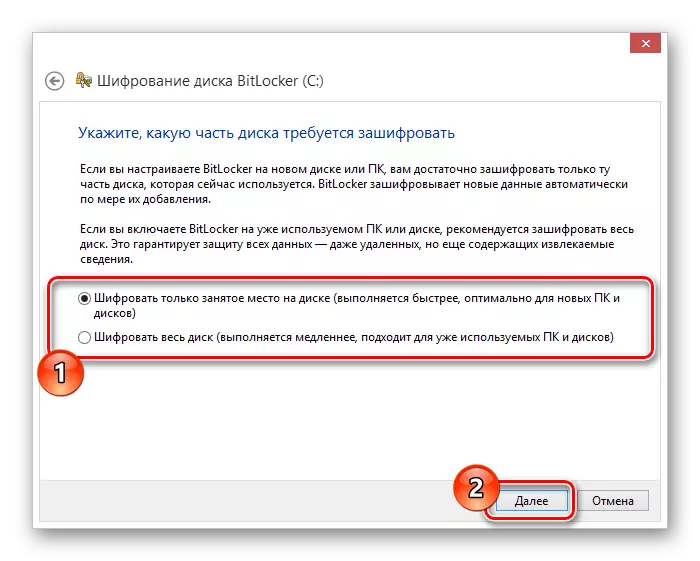

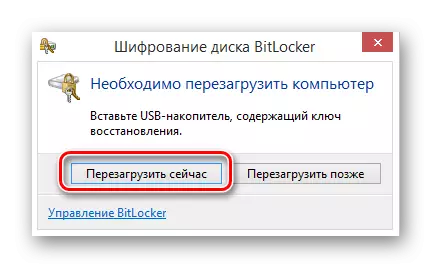
From this point on, the automatic data encoding process on the selected disk will begin, the time of which directly depends on the configuration of the computer and some other criteria.
- After a successful restart on the Windows taskbar, the data encoding service icon will appear.
- After clicking on the specified icon, a window will be presented with the possibility of transition to the BitLocker settings and a demonstration of information about the encryption process.
- Throughout the coding, you can easily use the processed disc.
- When the information security procedure is completed, a corresponding notification will appear.
- You can temporarily abandon the protection of the disk by using a special point in the BitLocker control panel.
- If necessary, changes can be paid to the beginning, using the "Disable BitLocker" item in the control panel.
- Disconnection, as well as inclusion, does not impose on you any restrictions in working with PC.
- The decoding may require more time than coding.

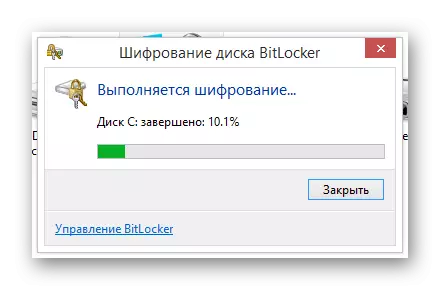
During operation, the Bitquer creates a sufficiently strong load on the disk. It is most noticeable if the system partition is handling.


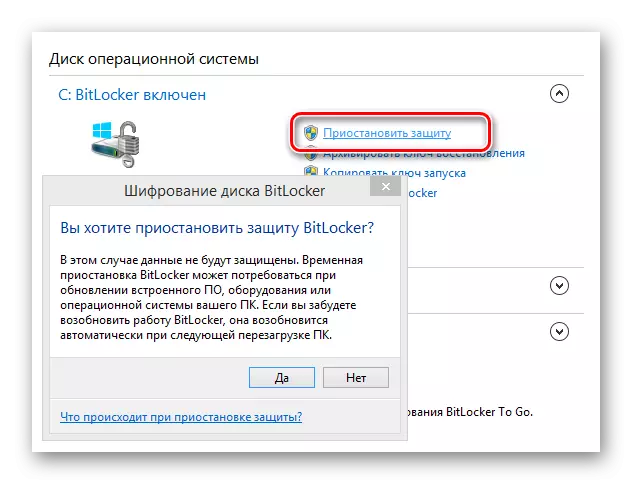
The performance of the protection system is resumed in automatic mode after turning off or restart your computer.
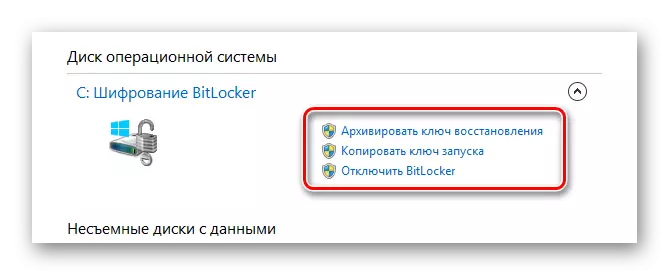

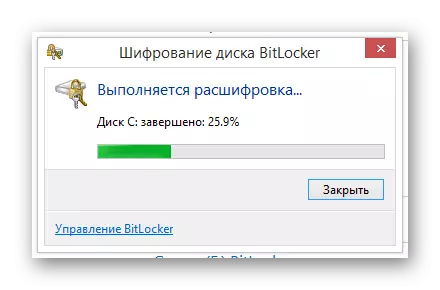
In the later stages of the encoding, the reboot of the operating system is not required.
Remember that now, when you have created some kind of protection of your personal data, you need to constantly use the available access key. In particular, this applies to the method using a USB drive to not meet with part-time difficulties.
READ ALSO: Folders do not open on the computer
Method 2: Sided Software
The second full-fledged method can actually be divided into many standards due to the existence of a huge number of different programs designed specifically to encrypt information on the computer. At the same time, as we have already mentioned at the very beginning, we revealed most of the software, but you can only decide on the application.
Please note that some high-quality programs are supplied by a paid license. But despite this, they have a fairly large number of alternatives.
The best, and that sometimes it is important, the most popular software for encryption is TrueCrypt. With this software, you can easily encode various information through the creation of special keys.
Another interesting program is R-Crypto, designed to encode data by creating containers. In such blocks, different information can be stored, it is possible to manage which is possible only if you have access keys.

The latter within this article, the software is RCF Encoder / Decoder, created in order to maximize the data encoding. Small weight of the program, a free license, as well as the ability to work without installation, are able to make this program indispensable for a regular PC user who is interested in protecting personal information.
Unlike the previously reviewed BitLocker functional, third-party software for encryption data allows you to encode only the information you need. In this case, the ability to restrict access to a whole disk also exists, but only in some programs, for example, TrueCrypt.
READ ALSO: Programs for encryption folders and files
It is worth drawing your attention to the fact that, as a rule, each application for encoding information on the computer has its own algorithm of relevant actions. Moreover, in some cases, the software has strict restrictions on the variety of protected files.
Compared to the same bit chiller, special programs cannot cause difficulties with access to data. If such difficulties still have arisen, we recommend that you familiarize yourself with the overview of the possibility of removing third-party software.
See also: How to remove a failed program
Conclusion
At the end of this article, it is quite important to mention the need to save the access key after encryption. Since if this key is lost, you can lose access to important information or a whole hard disk.
In order not to be problems, use only reliable USB devices and follow the recommendations given along the job.
We hope you received answers to coding questions, and we end up the topic of data protection on the PC.
