
Proxy is called an intermediate server through which the user is lost or the response from the end server. On this connection scheme can be known to all network participants or it will be hidden, which already depends on the purpose of use and type of proxy. The purpose of such technology there are several, and also it has an interesting principle of work that would like to tell you more. Let's immediately proceed to discuss this topic.
Proxy technical side
If you explain the principle of its operation with simple words, you should pay attention to only some of its technical features that will be useful to the usual user. The procedure for working through Proxy looks like this:
- You are connected to a remote PC from your computer, it acts as a proxy. It has a special software set, which is intended for processing and issuing appeals.
- This computer receives a signal from you and transmits it to the final source.
- Then receives a signal from the end source and transmits it back to you if required.
This uncomplicatedly operates the intermediate server between the chain of two computers. The picture below schematically shows the principle of interaction.
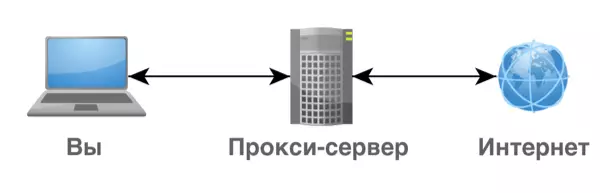
Thanks to this, the end source should not find out the name of the present computer, from which the request is made, it will only be aware of the proxy server. Let's still talk about the varieties of the technology under consideration.
Proxy servers species
If you have ever encountered using or already familiar with Proxy technology, they should have noticed that there were several varieties. Each of them performs a certain role and will be most suitable for use in different situations. Briefly tell about unpopular among ordinary users:- FTP Proxy. The data transfer protocol on the FTP network allows you to transmit files within the servers and connect to them to view and edit directories. FTP proxy is used to load objects to such servers;
- CGI reminds some VPN, but it's all the same proxy. The main purpose is its opening of any page in the browser without prior settings. If you found an anonymizer on the Internet, where you need to insert a link, and then the transition across it is most likely that such a resource worked with CGI;
- SMTP, POP3 and IMAP are involved in mail clients for mailing and receiving electronic letters.
There are three types with which ordinary users are often faced. Here I would like to discuss the most detailed as possible so that you understand the difference between them and chose suitable goals for use.
Http proxy
This species is the most common and organizes the work of browsers and applications using TCP Protocol (Transmission Control Protocol). This protocol is standardized and determining when installing and maintaining communication between two devices. The standard HTTP ports have a view of 8080 and 3128. The proxy functions simply simply - the web browser or software sends a request to open a reference to the proxy server, it receives data from the requested resource and returns them to your computer. Thanks to this HTTP proxy system allows:

- To make a caching of viewed information to quickly open it in the following times.
- Restrict user access to specific sites.
- Perform data filtering, for example, block promotional blocks on the resource, leaving an empty space instead or other elements.
- Set the limit on the connection speed with sites.
- Move the actions log and view user traffic.
All this functionality opens up many opportunities in different areas of work on the network, which are often facing active users. As for anonymity in the network, the HTTP proxy is divided into three types:
- Transparent. Do not hide the IP sender of the request and provide its end source. This species is not suitable for anonymity;
- Anonymous. Report the source on the use of an intermediate server, however, the client's IP does not open. Anonymity in this case is still not complete, since the output to the server itself will be able to find;
- Elite. Bought for big money and work according to a special principle when the final source does not recognize the use of proxy, respectively, the real IP of the user does not open.
Https proxy
HTTPs is the same HTTP, however, the connection is protected, as evidenced by the letter S at the end. Such a proxy is addressed if you need to transfer secret or encrypted data, as a rule, these are logins and passwords of accounts on the site. Transmitted information via HTTPS is not intercepted as the same HTTP. In the second case, the interception works through the proxy itself or at a lower access level.

Absolutely all providers have access to the transmitted information and create its logs. All this information is stored on servers and acts as evidence of action on the network. Personal data provides the HTTPS protocol, encrypting all traffic by a special algorithm that is resistant to hacking. Due to the fact that the data is transmitted in an encrypted form, such a proxy cannot count them and filter. In addition, it does not participate in decryption and any other processing.
Socks proxy
If we talk about the progressive type of Proxy, it is undoubtedly SOCKS. This technology was originally created for those programs that do not support direct interaction with the intermediate server. Now SOCKS has changed a lot and interacts perfectly with all types of protocols. The proxy type under consideration never opens up your IP address, so it can be considered absolutely anonymous.Why do you need a proxy server to the usual user and how to install it
In current realities, almost every active Internet user has come across various blockages and restrictions on the network. Bypassing such prohibitions and there is a basic reason why most users are looking for and installing a proxy to their computer or browser. Methods of installation and work There are several, each of which implies the implementation of certain actions. Check out all ways in our other article by clicking on the following link.
Read more: Configure connection through a proxy server
It is worth noting that such a connection can be a little or even significantly reduce the Internet speed (which depends on the location of the intermediate server). Then periodically need to turn off the proxy. Expanded manual for the implementation of this task, read further.
Read more:
Disabling the proxy server in Windows
How to disable proxy in Yandex.Browser
Choice between VPN and Proxy server
Not all users were delighted into the topic of distinguishing VPN from proxy. It would seem, they both change the IP address, provide access to blocked resources and provide anonymity. However, the principle of operation of two these technologies is completely different. The advantages of the proxy consist in the following features:
- Your IP address will be hidden at the most superficial checks. That is, if the case does not occur special services.
- Your geographical position will be hidden, because the site receives a request from an intermediary and sees only its position.
- Certain proxy settings produce competent traffic encryption, so that you become protected from malicious files from suspicious sources.
However, there are also negative moments and they are as follows:
- Your Internet traffic is not encrypted when passing through an intermediate server.
- The address is not hidden from competent methods of detection, so if necessary, your computer can easily find.
- All traffic passes through the server, so it is possible not only reading from its part, but also interception for further negative action.
Today we will not go into the details of the VPN work, we note only that such virtual private networks always take traffic in an encrypted form (which affects the connection speed). At the same time, they provide better defense and anonymity. At the same time, a good VPN is more expensive proxy, since encryption requires large computing power.
See also: Comparison of VPN and hidemy.name service proxy servers
Now you are familiar with the basic principles of work and the purpose of the Proxy server. Today, the basic information was considered, which will be the most useful for an ordinary user.
See also:
Free Install VPN on Computer
Types of connections VPN.
