
Many users of computers spend the most time in browsers using it in service or working purposes. Naturally, this factor is critical for intruders who will try to do everything to infect a custom web browser, and the computer itself. If you suspect that this happened and with your WORKER on the Internet, it's time to check it.
Viruse browser check
There is no one variant of infection, in which the user can safely go and get rid of malicious software. Due to the fact that the varieties of viruses are different, it is necessary to check several vulnerable places used for infection at once. We will analyze the main available options for the browser can be attacked.Stage 1: Check for miners
Already the first year is relevant to the type of malicious code working as Mainer. However, it works, of course, not on you, but on the one who used this code against you. Mining is the process of mining cryptocurrency, where the computational abilities of the video card are involved. People who are engaged in this usually use their own video cards, of which they create entire "farms" (combining the most powerful video card models), accelerating profit production. Not the most honest of them decide to go easier, not spending great money to buy equipment and pay for electricity that these video cards are consumed within a month. They infect computers of random people on the Internet by adding a special script to the site.
It looks like this process as if you went to the site (it can be informative or empty, as if abandoned or not developing), but in fact, the insistentible for you is launched by mining. Often inexplicably the computer begins to slow down, and it stops if you close the tab. However, this option is not the only outcome of events. Additional confirmation of the presence of a miner can be the appearance of a miniature tab in the corner of the screen, deploying which you can see an almost empty sheet with an unknown site. Often, users may not even notice that it is launched - on the fact that the whole calculation. The longer the tab is launched, the more Profit from the user received a hacker.
So, how to recognize the presence of Mainer in the browser?
Check via web service
Opera developers have created a Cryptojacking Test web service that checks the presence of hidden miners in the browser. You can pass it using any web browser.
Go to Cryptojacking Test
Follow the link above and click the Start button.
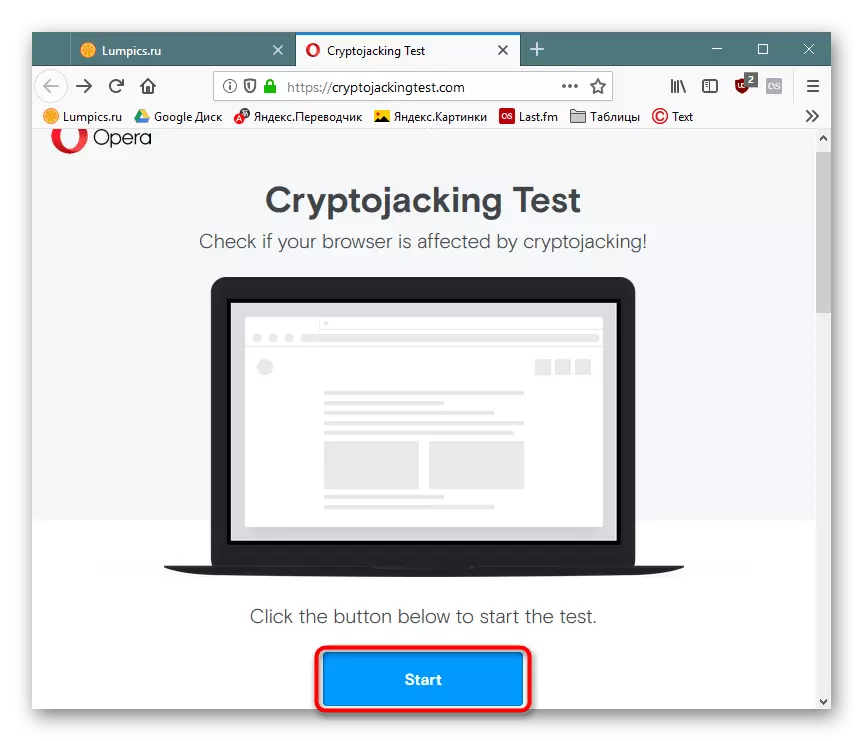
Wait for the procedure to be completed, at the end of which will receive the result of the browser state. When displaying the "You're Not Protected" status, you need to manually take action to correct the situation. However, it is worth keeping in mind that it will never be rejected by the indicators of this and such services by 100%. For complete confidence, it is recommended to perform the actions that are described below.
Check tab
Look at the "Task Manager" built into the web browser and check how many resources are consumed tabs.
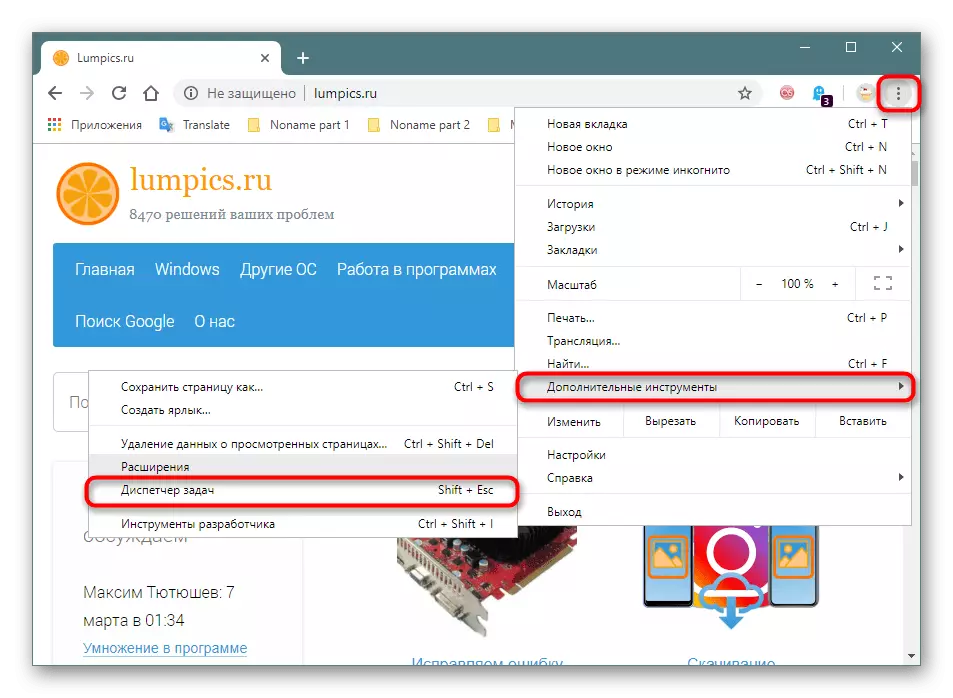
Browsers on Chromium (Google Chrome, Vivaldi, Yandex.Browser, etc.) - "Menu"> "Advanced Tools"> "Task Manager" (or press the SHIFT + ESC key combination).
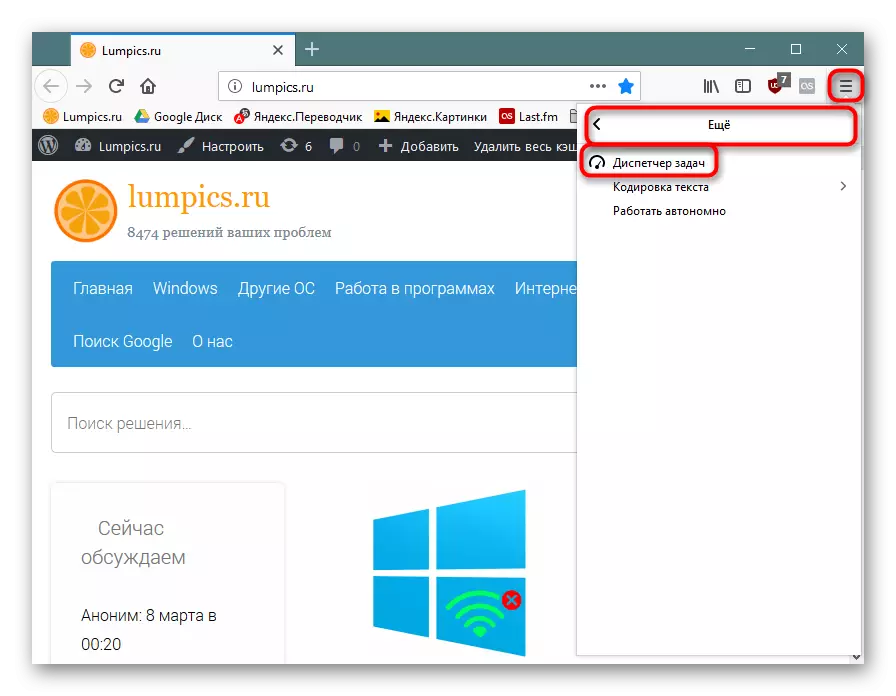
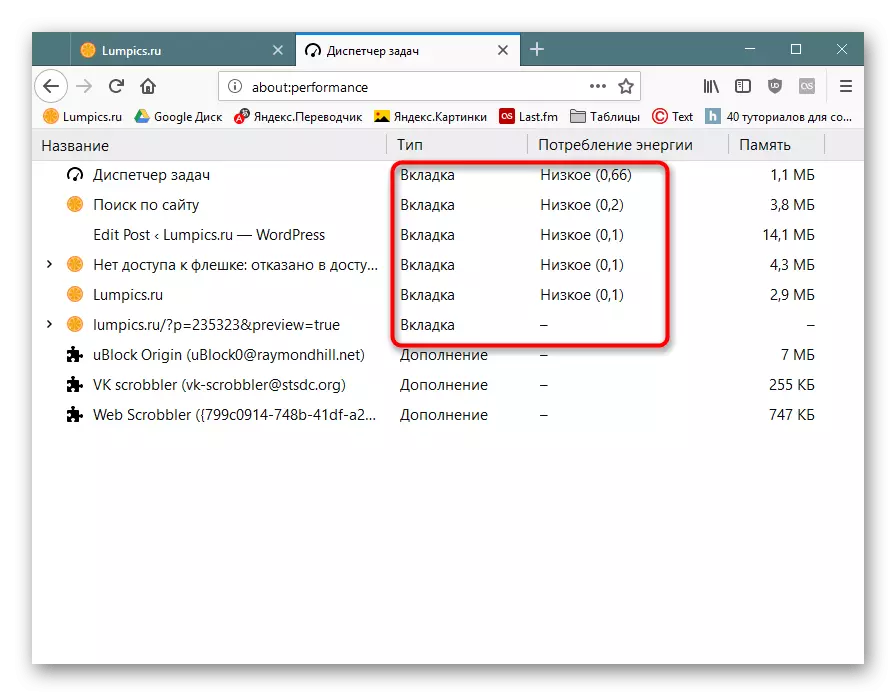
Firefox - "Menu"> "More"> "Task Manager" (or enter About: Performance in the address bar and press ENTER).
If you see that some kind of resource tab is used quite a lot (this is noticeable by the CPU column in Chromium and "Energy Consumption" in Firefox), for example, 100-200, although in the normal value of 0-3, then the problem is really , exists.
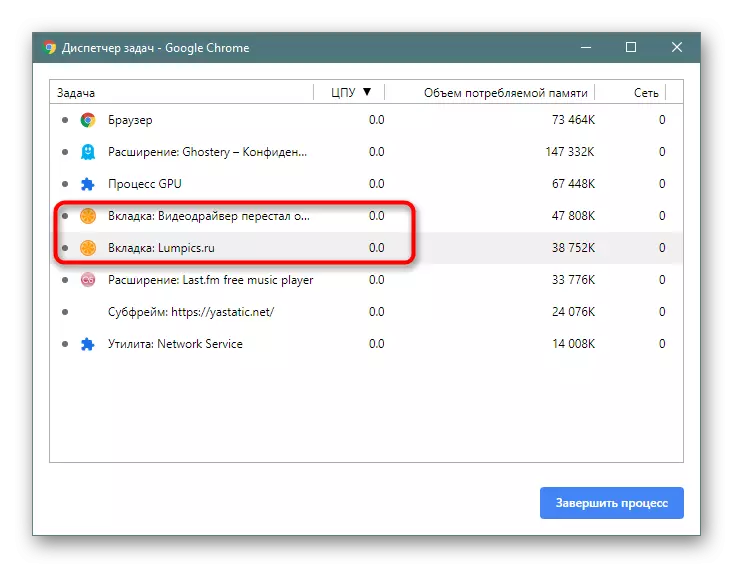
We calculate the problem tab, close it and do not go to this site anymore.
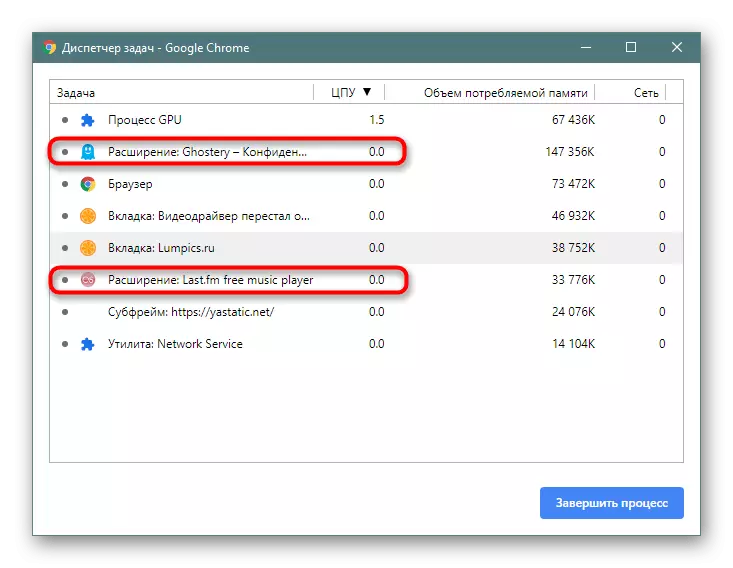
Expansion checks
Mainer does not always lift on the site: it can be in the established expansion. And you will not always know that it is generally installed. It can be recognized in the same way as the Mainer tab. Only in the "Task Manager" this time, see not a list of tabs, but launched extensions - they are also displayed as processes. In Chrome and its analogs, they look like this:
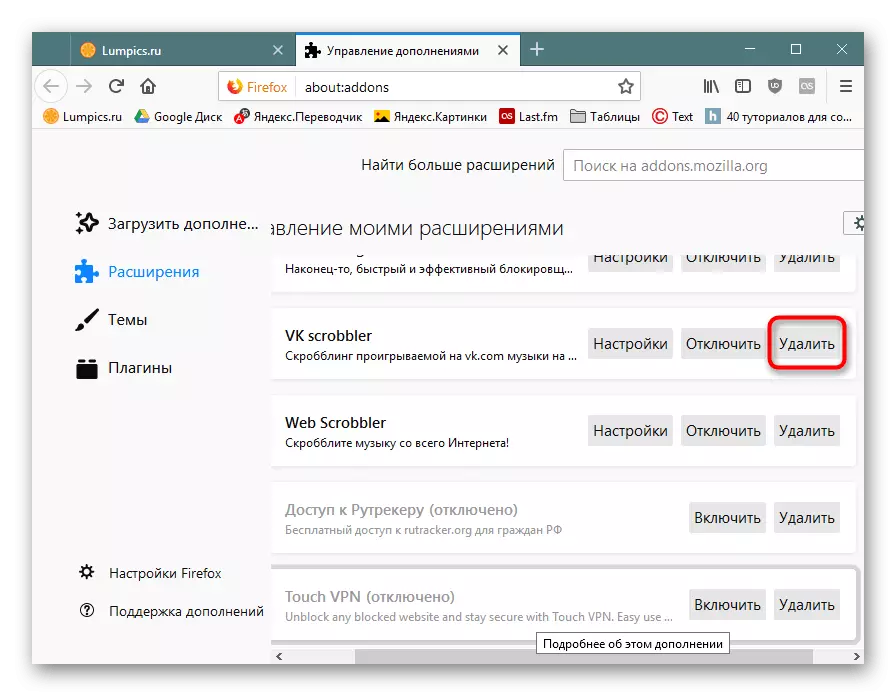
In Firefox, the type "Supplement" is used for them:
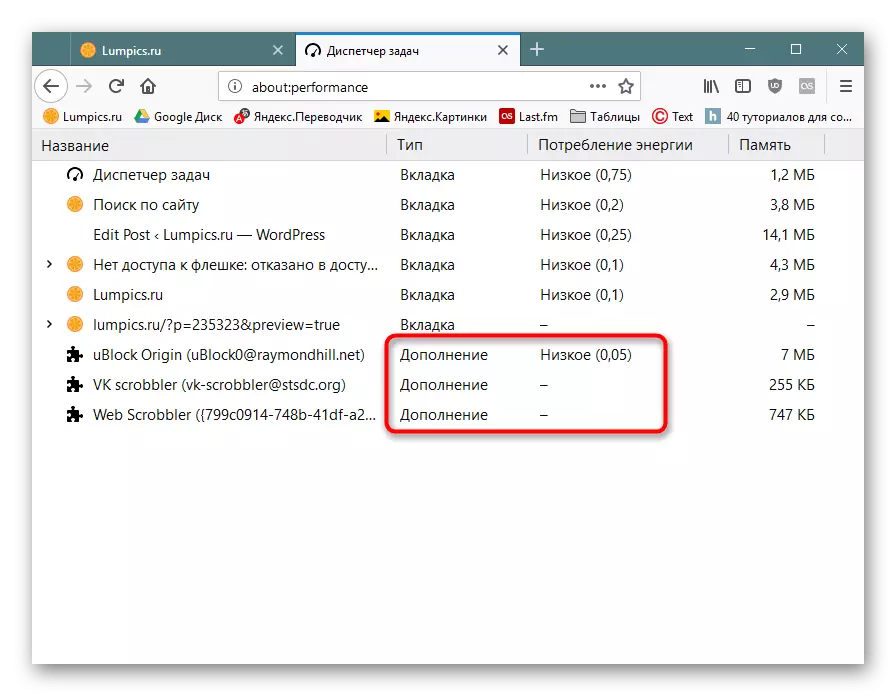
However, not always mining will be launched at the moment when you are watching "Task Manager". Go to the list of installed add-ons and browse their list.
Chromium: "Menu"> "Additional tools"> "Extensions".
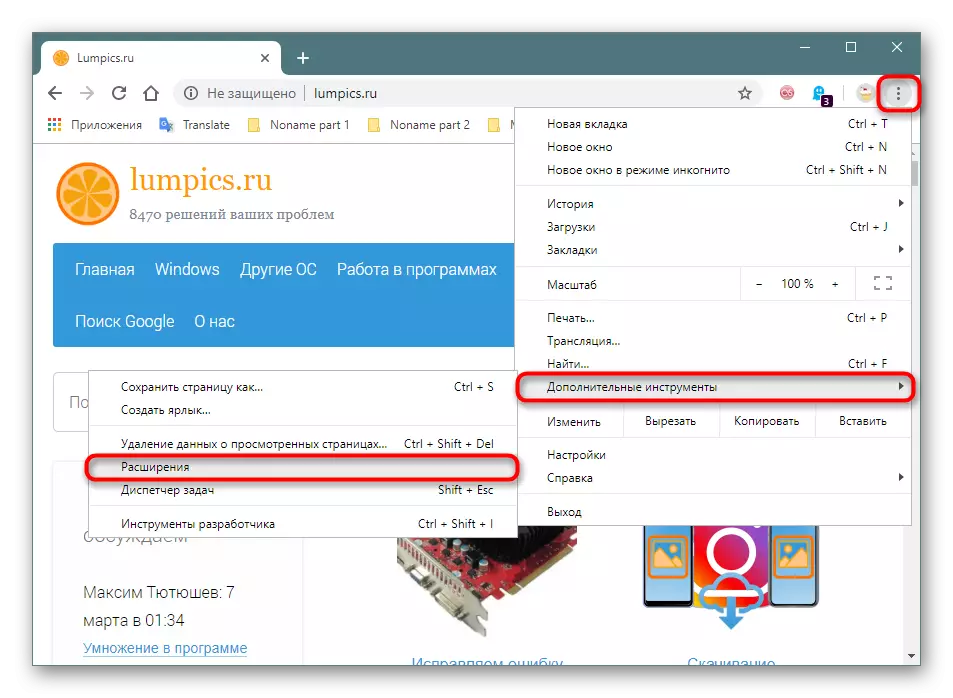
Firefox - "Menu"> "Supplements" (or press Ctrl + Shift + A).
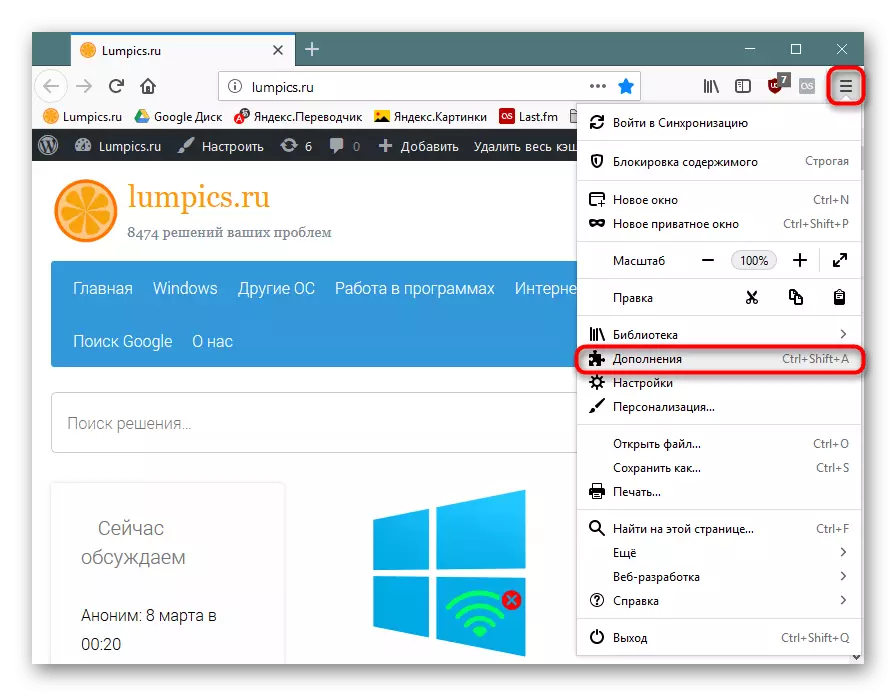
Browse the list of extensions. If you see some kind of suspicious, which you are either not installed, or simply do not trust it - delete.
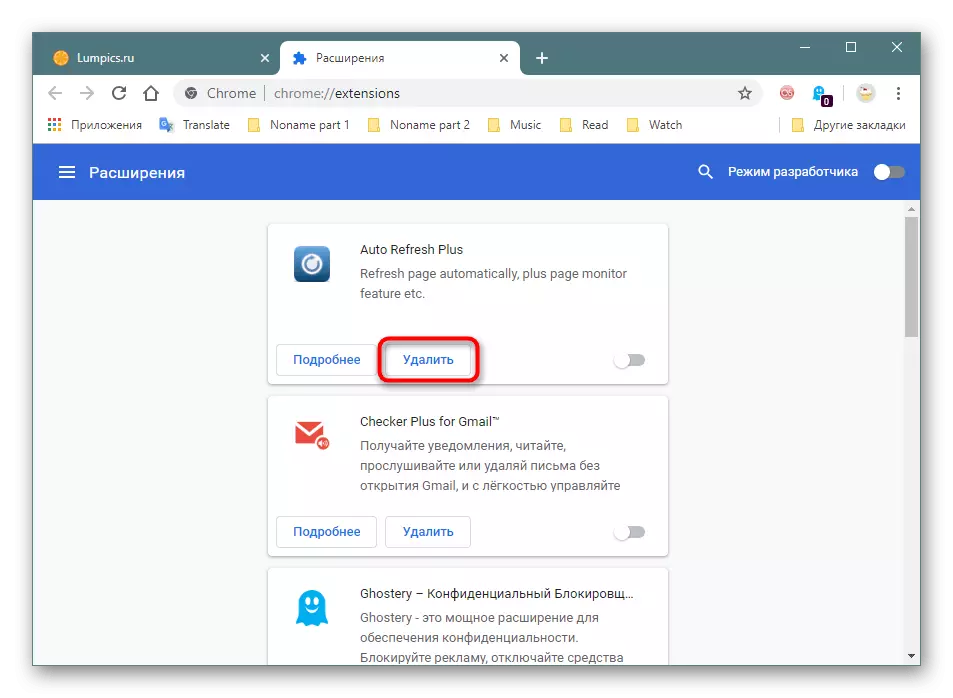
Even if there is no Mainer, there may be other viruses in unknown extensions, for example, kidding user data from some account.
Stage 2: Check Label
The format of the browser label (and any other program) allows you to finish the properties to add certain parameters, together with which it will start. This is usually used in order to expand functionality or troubleshooting, for example, with the content of the content, but the attackers can be added autorun a malicious executable file, which is stored on your PC in the form of BAT, etc. Run change variations can be more innocent, aimed at displaying advertising banners.
- Click on the browser label with the right mouse button and select "Properties".
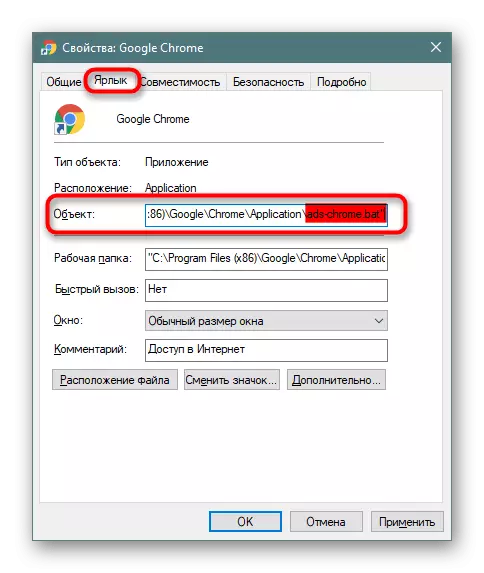
- In the tab "Label", find the field "Object", view the line to the end - it should end in one of the following options: Firefox.exe "/ chrome.exe" / opera.exe "/ browser.exe" (Yandex.Browser).
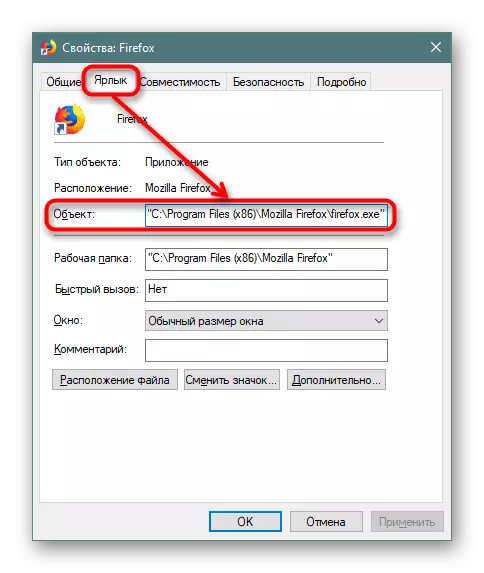
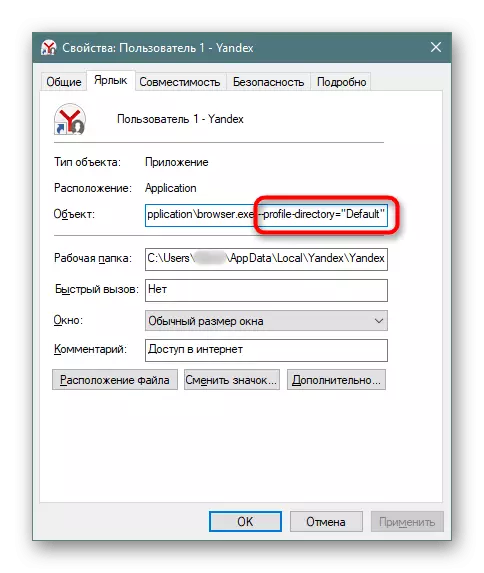
If you use a browser separation function to profiles, at the end it will stand the attribute like this: --Profile-Directory = "Default".
- When you try to change the work of the browser, you can see inconsistencies with the examples above. For example, instead of chrome.exe, it will be spelled out something like what you see in the screenshot below. The easiest way is to remove this shortcut and create a new one. To do this, you will need to go to the folder where the EXE file is stored, and create a label from it yourself.
- As a rule, in the properties of the "Operating Folder" list, it is correct, so you can use it to quickly search the browser directory.
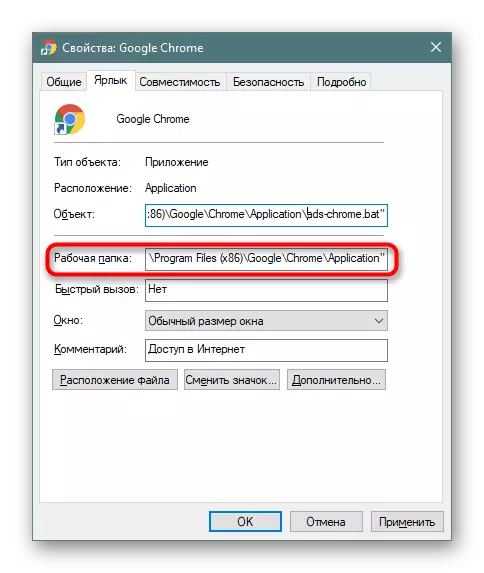
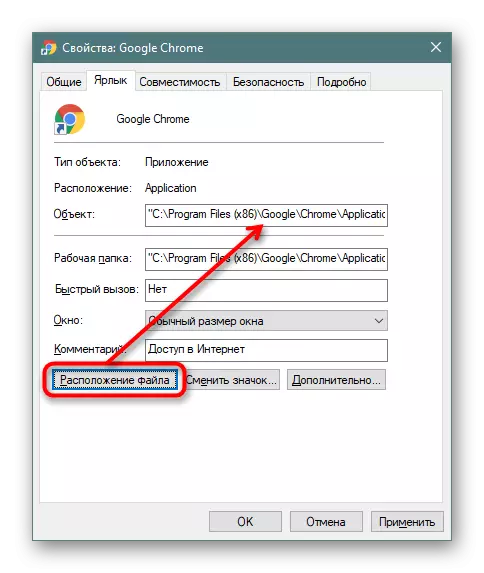
In addition, you can click on the "Location of the File" to quickly go to it, but provided that the fake file is in the browser's working folder (you can learn about this from the "Object" field).
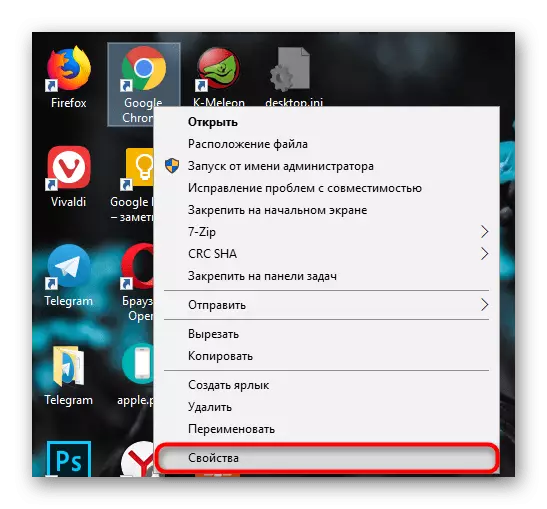
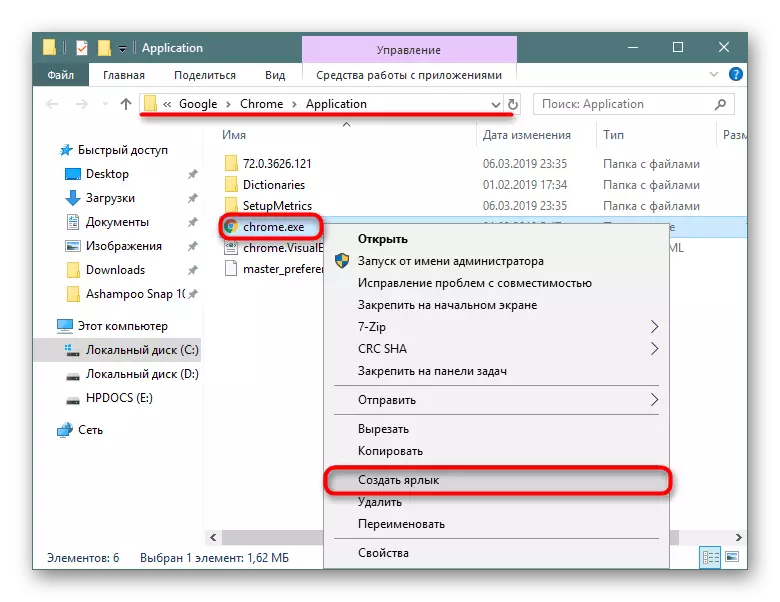
- We delete the modified file, and create a shortcut from the EXE file. To do this, click on it right mouse button and click "create a shortcut".
- It remains to rename it and drag it there, where there was an former label.
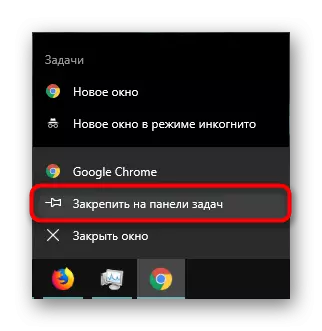
- If you do not need a shortcut, you can start the browser and secure it on the taskbar.
Stage 3: Computer Scanning
No matter how to scan the computer for not only viruses, but also just an undesirable software that loves to register in the browser in the form of Tulbarov, search engines by default, banners, etc. Different developers were created at once several utilities that detect malicious software, forcing, for example, to replace the search engine, open the browser independently, display advertising in a new tab or in the wind corners. With a list of such solutions and lessons on their use, as well as with information on troubleshooting, in which the web browser opens at any time at any time, you can read the articles on the links below.Read more:
Popular advertising programs in the browser
Fighting advertising viruses
Why the browser starts independently
Stage 4: Cleaning Hosts
Often users forget to look into the tool directly controlling access to anyway or other sites. Sites are often added to the hosts file, which are later running in a web browser against the will of the person. The cleaning process is not difficult, for this locate and change the file to the following instruction.
Read more: Change Hosts File in Windows
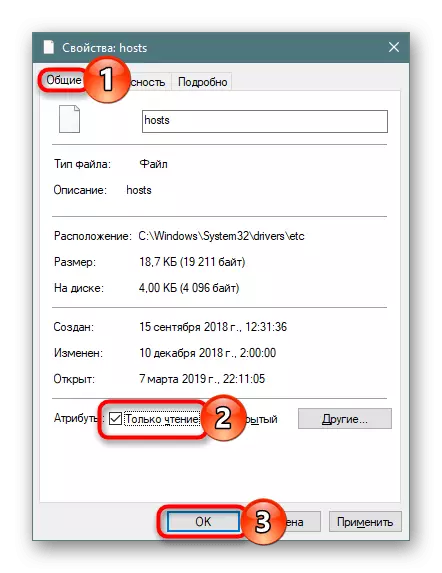
You need to bring HOSTS to the same state as the screenshot of the article on the link above. Take into account a couple of nuances:
- Especially curtail add lines with sites to the bottom of the document, leaving the visible field blank. Be sure to see if the scroll bar is on the right side.
- In the future, the document can easily change any hacker without any problems, so it will be a good option to make it read-only (PCM by Hosts> "Properties"> "Only reading").
Stage 5: View the list of installed programs
Some programs are not defined as advertising or unwanted, but in fact are such for the user. Therefore, carefully inspect the list of installed software, and if you see an unfamiliar application that you are not installed, find out its value. Programs with names in the Spower "Search", "Toolbar" and need to be removed without thinking. They will definitely not bring any benefit.
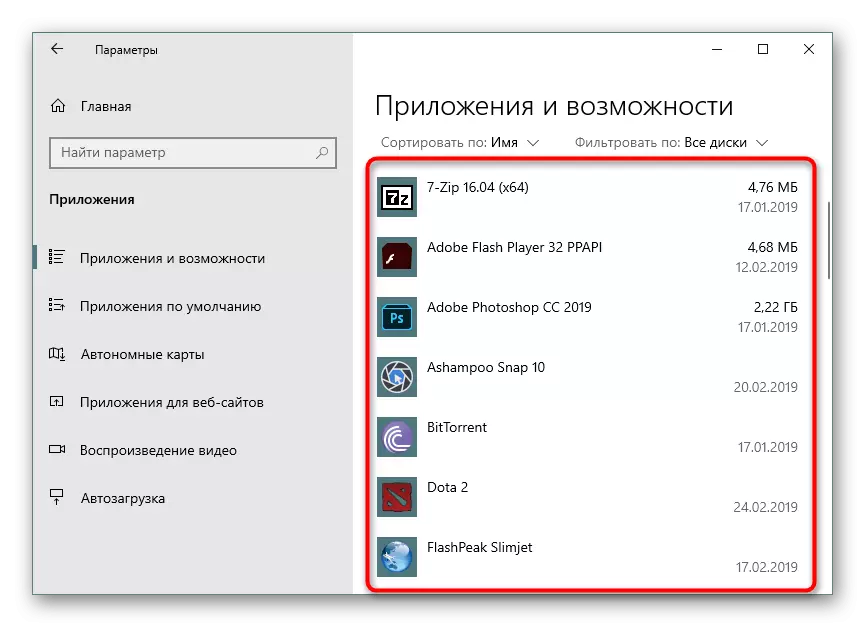
READ ALSO: Ways to remove programs in Windows 7 / Windows 10
Conclusion
We disassemble the main techniques of checking and cleaning the browser from viruses. In the overwhelming majority, they help either find a pest, or make sure it is not. Nevertheless, viruses can sit in the cache of the browser, and check it on clean, except the scanning of the cache-cache folder does not seem possible. For prophylaxis or after accidental download, the cache virus is highly recommended to clean. Make it easy to use the following article.
Read more: Cleaning cache in browser
Advertising blocker extensions help not only remove annoying browsers, but also block the aggressive behavior of some sites arresting to other pages that may be malicious. We recommend Ublock Origin, you can choose another option.
If even after all checks, you notice that something is happening with the computer, most likely, the virus is not in the browser, but in the operating system itself, managing, including it. Be sure to scan the entire computer using the recommendations from the reference manual below.
Read more: Fighting computer viruses
