
Now many users actively use removable USB drives where private and confidential information is sometimes stored. Ensuring such data is an important procedure that allows you to save files in secrecy and avoid their reading by intruders or unwanted persons. All this is feasible with the help of special methods we want to talk about.
Perform data encryption on flash drive
There are different ways to protect the available files on the drive, for example, you can put a password or to establish a hide, but all this does not allow one hundred percent protection, but in certain situations it is considered a good option. We propose to consider several ways - from the simplest to the difficult, but most reliable. After familiarization with the instructions, you can already choose the optimal solution.Method 1: Setting the password to files
The first method is the easiest and fastest, accordingly, not ensuring proper protection from reading. If necessary, an experienced attacker or an advanced user will select the content disclosure option. Installing a protective code to files is recommended if you want to avoid opening data from other users of this flash drive or, for example, to protect them from the child. Detailed instructions for adding a password on the example of two popular programs can be found in other articles on the following links.
Read more:
Installing a password to files in Microsoft Excel
Method 2: Installation of the password on the USB flash drive
Installing a password on a USB drive is an already more serious solution, but is suitable only in those situations where absolutely all the contents of the carrier must be encrypted. Then you can not do without the use of special software, which is in free access on the Internet or applies for a fee. Each software uses its encryption and protection techniques, which makes it possible to ensure the security of files on the flash drive, but they can all also be hacked with certain knowledge of vulnerabilities. Expanded information with the description of the most popular according to you will find in a separate material further.Read more: Instructions for protecting flash drive password
Method 3: Veracrypt
The program called Veracrypt is considered to be one of the most reliable and effective tools for performing various encryption of flash drives. Its functionality includes the creation of a simple encrypted volume, the premises of the hidden volume in the already created section or complete processing of the drive. The user only needs to make a choice of data protection. We offer to familiarize yourself with all the options in more detail.
Installation and Starting
We would have gained the installation procedure by the party if it had not had certain nuances affecting the further efficiency of the software under consideration. Therefore, we recommend installing in accordance with the following instruction.
Go to the official site of the VERACRYPT program
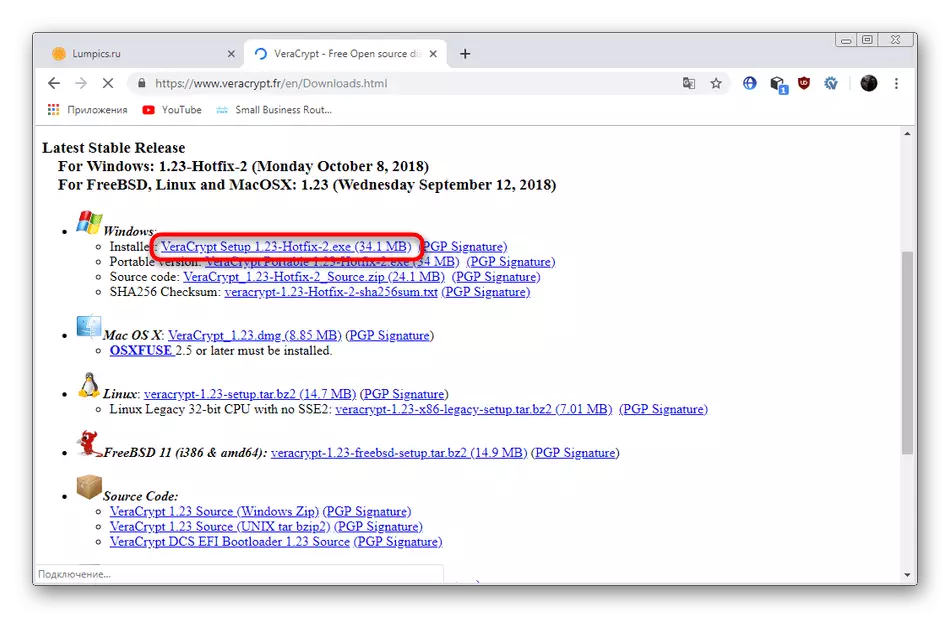
- Navigate to the official website of Veracrypt, using the reference above. There, click on the inscription highlighted blue to start loading the installer.
- Wait for downloading and run the executable file.
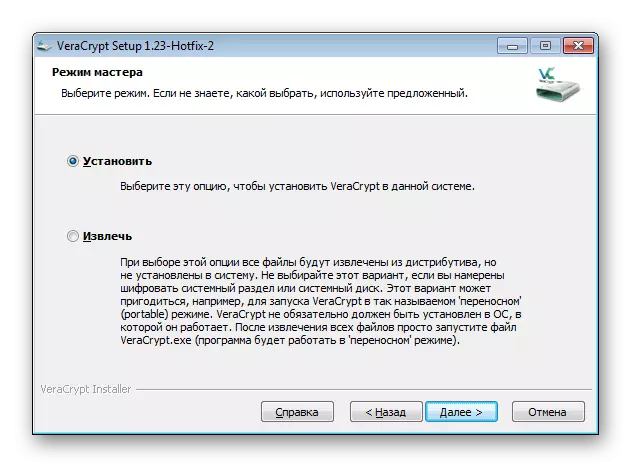
- You are offered two actions to choose from - installing or removing software. If you wish to encrypt the USB flash drive and then read it on any device, select "Extract" to further specify the location of the device. The "Set" parameter is suitable for those who want to use the software within the same operating system.
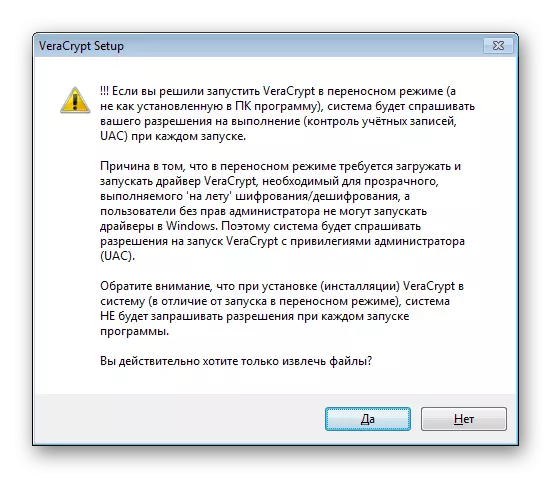
- You will be familiarized with the launch warning if you specify it.
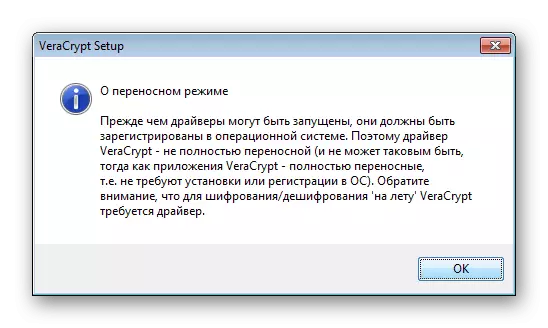
- In addition, a notification will be notified about the features of the launch of the portable version.
- It remains only to specify the location to install the program.
- Play the installation and proceed to the directory with VeraCrypt.
- Start the EXE file in accordance with the installed version of the OS. For example, for 32-bit Windows, you need to select the file "Veracrypt", and for 64 - "VeraCrypt-X64".
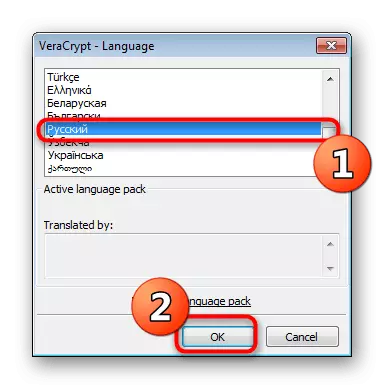
- After launching the interface will be in English. Change it through "Settings"> "Language".
- Select another suitable language and click on "OK".


After that, the program is considered completely ready to perform further encryption of the existing drive.
Option 1: Creating an encrypted file container
Veracrypt uses various encryption types that apply to specially made volumes. Such a section indicates a separation of a certain number of flash drive space with a further record of files on it. Displaying volumes and access to saved objects there will be available only after mounting through the same program, before that the partition itself will be shown on the flash drive as a file without a format. As for the creation of a new volume, it is done like this:
- Run the program and click on the "Create Tom" button.
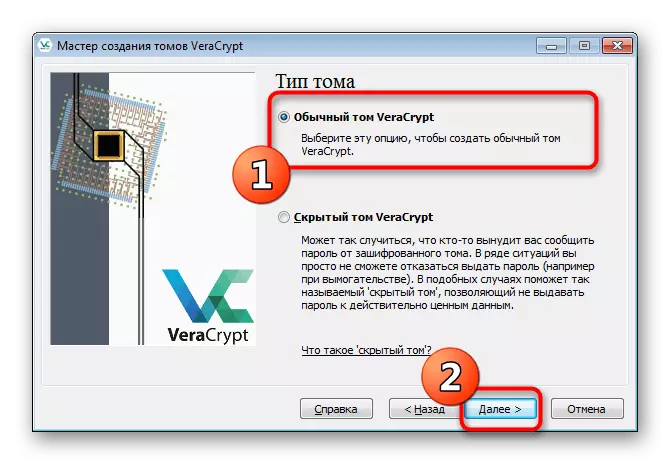
- Mark the point "Create an Encrypted File Container" item and click on "Next".
- Specify the type of volume "Normal Tom Veracrypt" and go to the next step. We will talk about hidden volumes a little later.
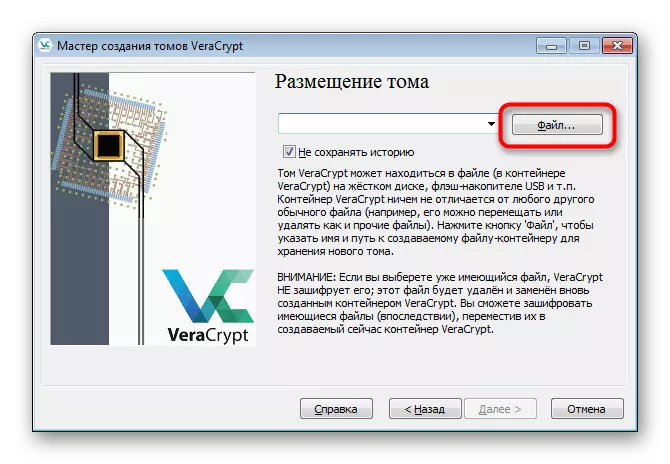
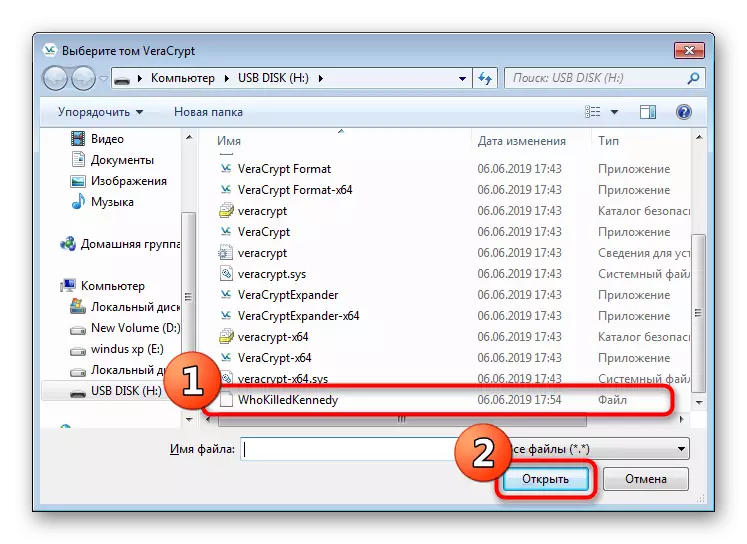
- It will takes a container itself. To do this, click on the File.
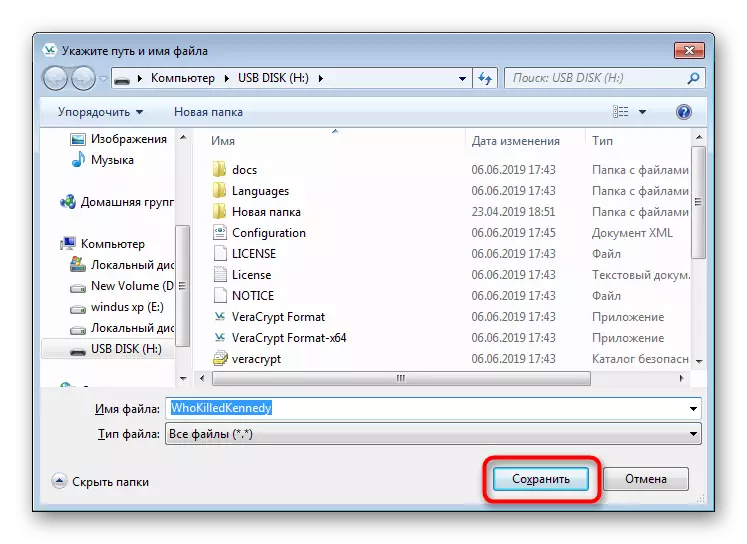
- Create an object with an arbitrary name on the flash drive and save it.
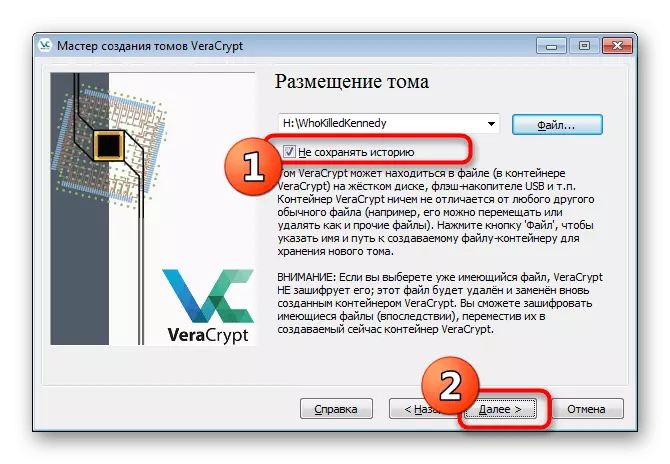
- Tick the "Do not save history" checkmark and follow further.
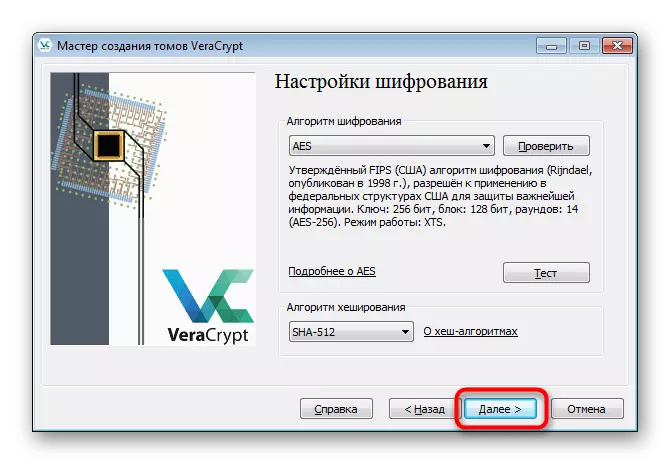
- You will need to specify the protection and hashing method. If you do not understand the subject of cryptography, just leave all the default values. In the same window, there are buttons by clicking on which you will enter the page on the Internet with explanations of all encryption and hashing algorithms.
- Set volume size. It should not exceed the entire amount of free space on the USB flash drive.
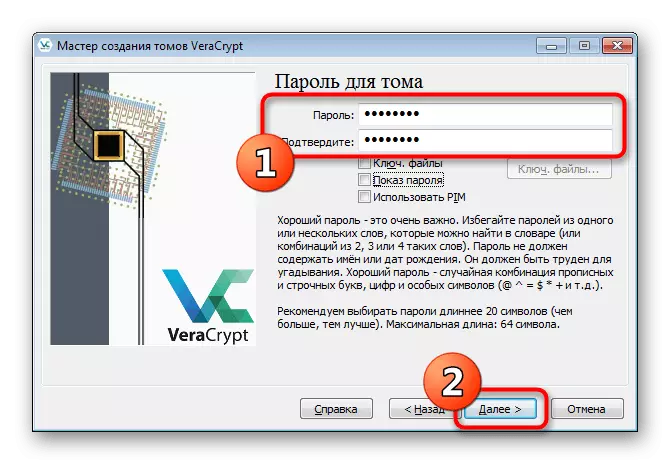
- Set the password to access that. This window below contains recommendations for choosing a reliable keyword.
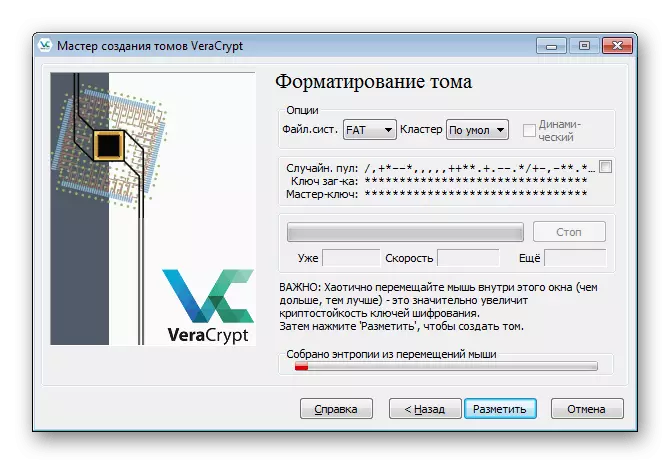
- The cryptoposticness of encryption keys depends on the saving of random actions, which will be said when the volume formatting window is displayed. You will need to set the file system and move the mouse cursor inside the window so that Veracrypt collected random information and recorded them in the encryption key. It is possible to do this until the strip "assembled entropy from mouse movements" will not become green.
- After that, click on "place".
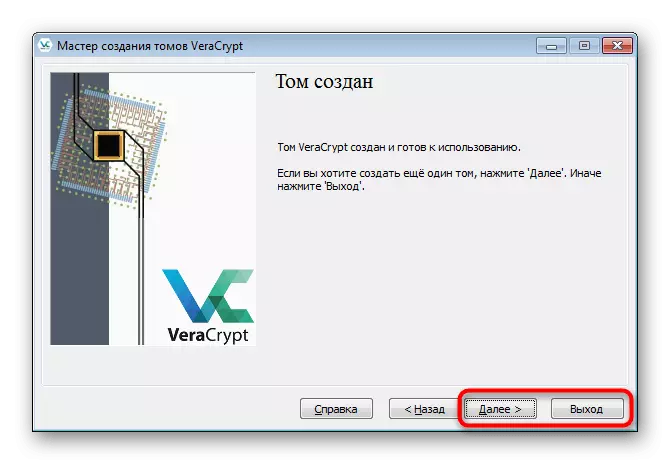
- Upon completion of the creation of Tom, you will receive the appropriate notification and you can make another partition or exit the wizard.
- Now on the flash drive you see the volume itself in the form of a file without a format with the specified size.




You have access to such volumes to the creation of such a moment as the free place on the drive is not completed. Additionally, it is proposed to choose absolutely any size of the virtual partition, even 10 KB.
Next, the container is mounted, after which it is displayed in the operating system as a virtual drive. Then you can copy all the important items that you want to save. Mounting and further work with the drive looks like this:
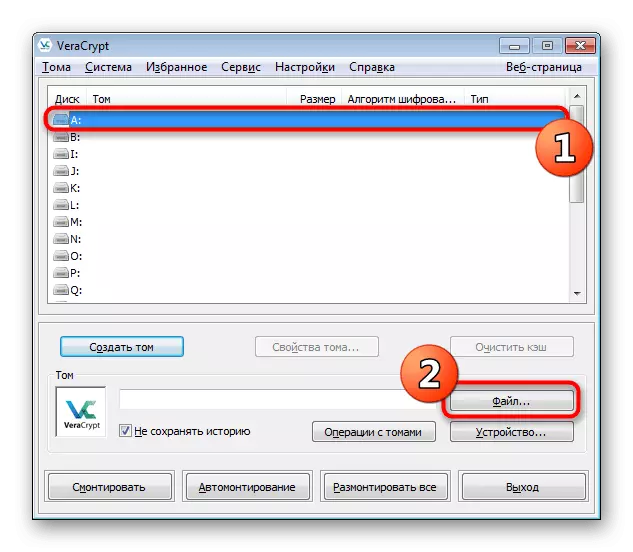
- Specify any free drive in Vera and click on the file.
- In the observer that opens, go to the flash drive and open the earlier element.
- Click the "Mount" button.
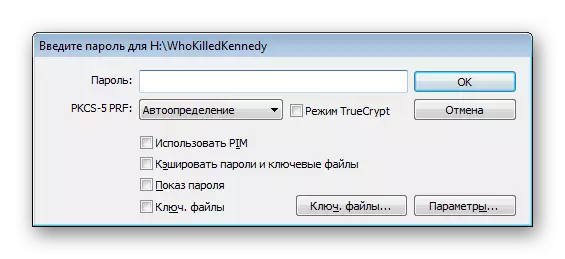
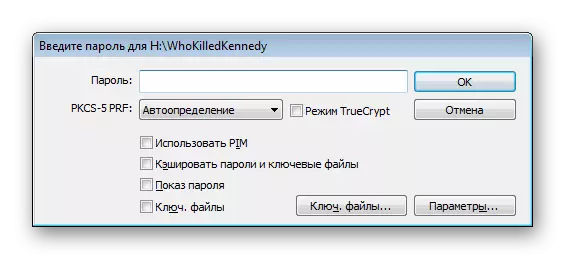
- After the window appears with the form for entering the password. Write it in the appropriate field.
- The mount procedure itself will take a few minutes, and during this process the program may not respond.
- Now go to "This computer" to see the new section. Move there any desired objects.
- Do not forget at the end of all actions, be sure to unmount the drive so that after rebooting the operating system there are no problems.
- An empty disk appeared on the successful conduct of this operation.


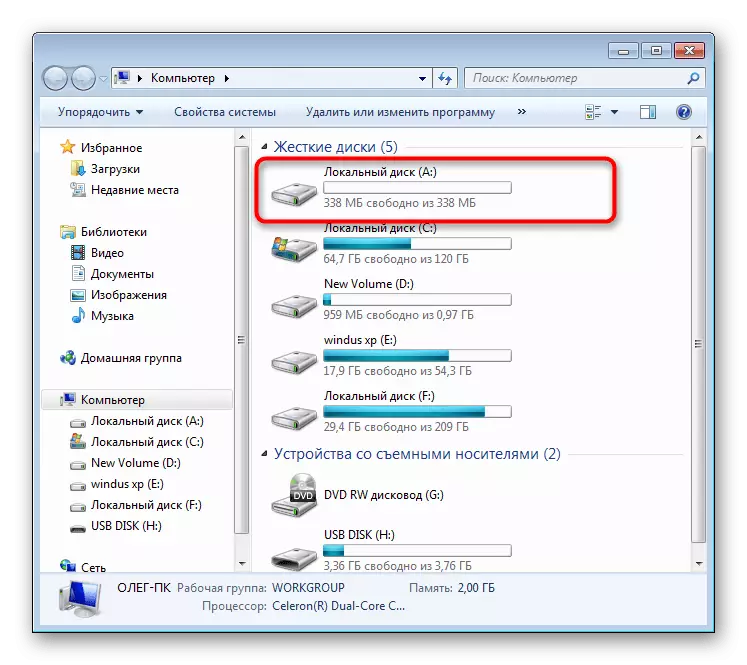
Now all your files that have been placed in a virtual disk created through the software in question are securely protected by password and will be available for viewing and deleting only after successful mounting.
Option 2: Creating a hidden volume
Hidden tom is more and more protection of very important files. Its principle is that the user creates a section within the created partition and indicates a new password for it. When you connect to the usual, it is proposed to enter a password if you specify the key from the hidden container, the transition to it will automatically happen, and not in the first partition. To make such encryption, first familiarize yourself with the previous instruction, and then go to the specified below.
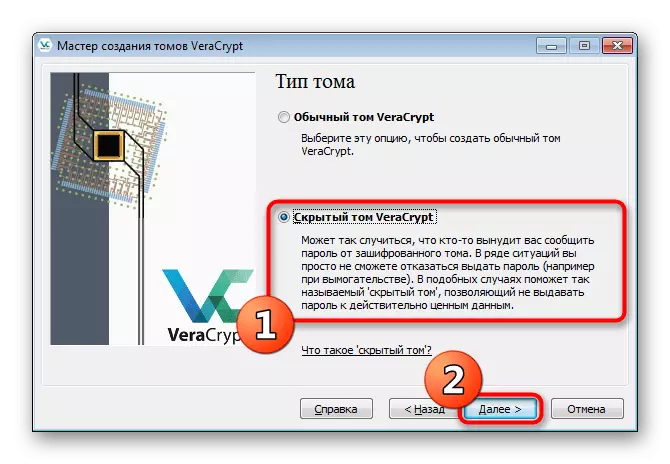
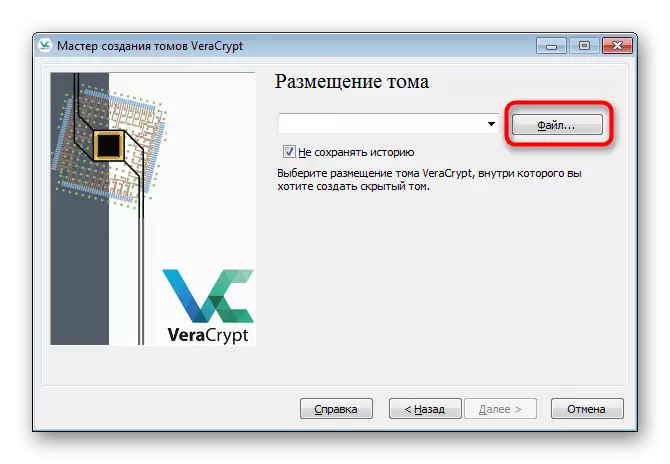
- Open the volume creation wizard and select "Hidden Tom".
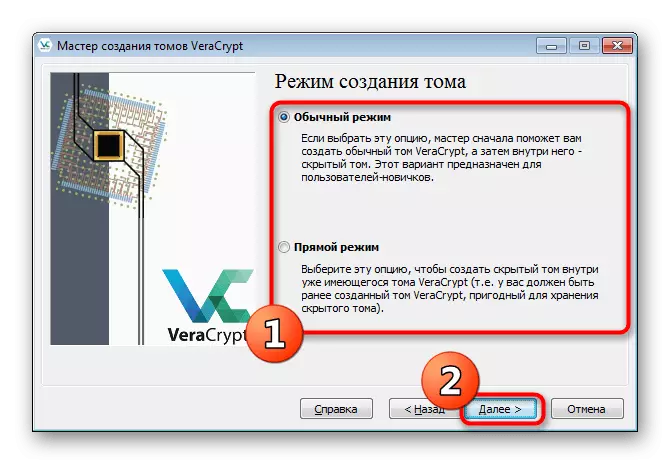
- If you have not yet created a regular container, mark the "Normal Mode" marker. In the event of its presence, specify "direct mode".
- Go to the selection of a normal volume file.
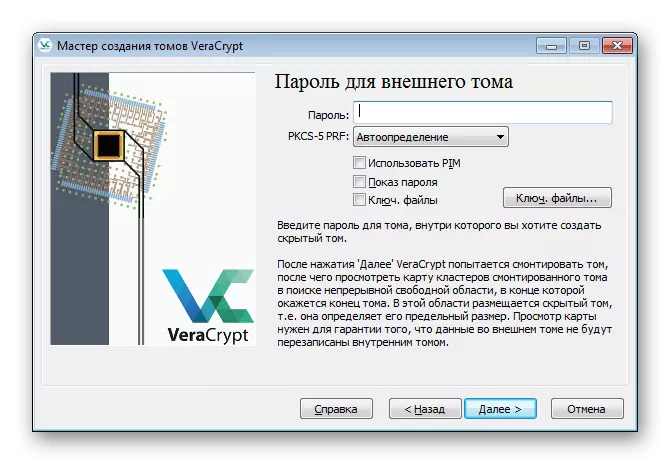
- Enter the password from it to get the opportunity to create inside the hidden volume.
- After the Wizard of the Creation of Hidden Tom will appear. The sequence of actions is no different from the external container, so just follow the already known guide.
- Upon completion, you will receive a notice that the hidden volume is ready to use.
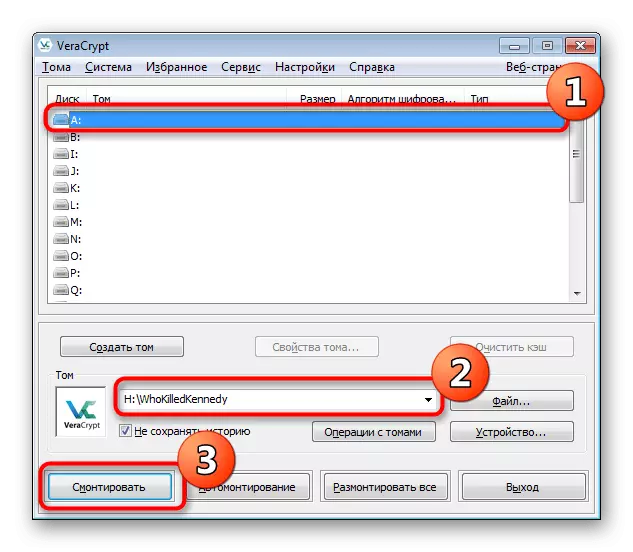
- During the disk mount, select the previously created external container file.
- However, when entering the password, write the key from the hidden volume.
- A successful connection to it will indicate the inscription "Hidden" in the Type column.

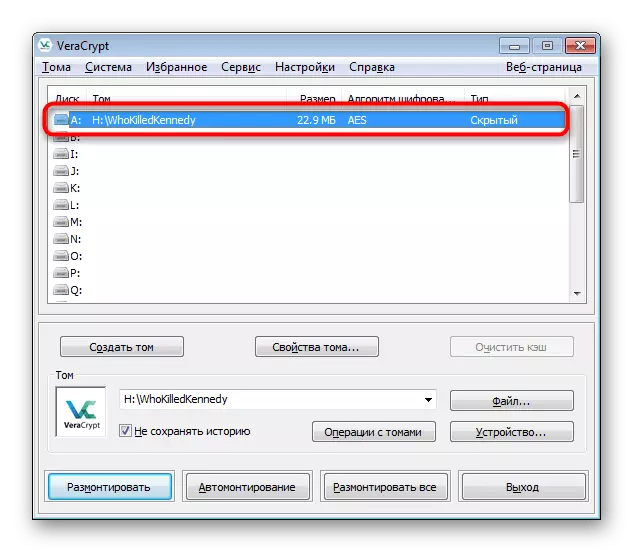
Further work with a hidden container is carried out on the principle of interaction with external - you also go to it through the "Explorer" and place the most important objects for maximum protection.
Option 3: flash drive encryption
Some users do not suit the method of creating containers, since the priority is the encryption of the entire contents on the carrier. Considered today will help in this. The flash drive encryption algorithm is almost no different from the creation of containers, but has mandatory nuances.
- Run the program and go to the wizard by clicking on the "Create Tom" button.
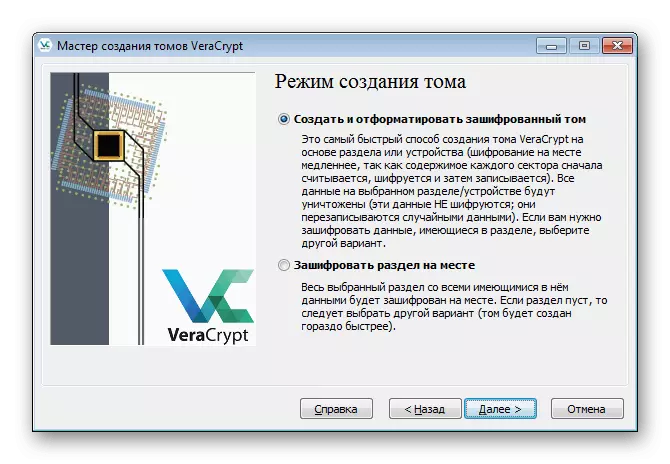
- Mark the marker item "Encrypt the non-system / disk" and click on "Next".
- Create a normal volume.
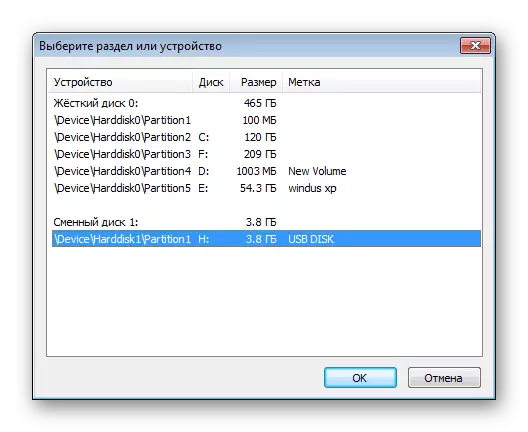
- Click on the "Device" button to proceed to the selection of flash drives for encryption.
- After opening the window, find the appropriate removable disk.
- You are invited to create a new volume and format it or execute encryption, leaving available files. The second method will take much more time, so in the absence of files, you should specify "create and format the encrypted volume".
- All other actions are made in the same way as in the case of containers - the password is configured, the type of encryption, and then the formatting process is started. The same applies to the mount


You should mark one item - now when you connect a flash drive to a computer, a notification will appear "Before using the disk in the drive, it must be formatted." At this stage, be particularly vigilant, because it is always necessary to reject this offer. After cancellation, start the veracrypt and mount the drive through it, only then it will be correctly displayed in the system and the files will become available for operation.
Today you have been familiar with the data encryption methods on the flash drive. Most of all the attention was paid to a unique software called VeraCrypt. This decision offers the user several types of information protection, so everyone can find the perfect way for itself. It is very important to take into account all the steps of instructions in order to accidentally prevent errors and not lose all the files.
