
The cryptocurrency boom of 2017 has led not only to a significant rise in price of video cards and the basis of many cryptoferms and stock exchanges. The negative impact on the broad masses of users was expressed in the fact that they, and specifically, on computational capacities, their PCs without the knowledge of the users themselves decided to earn hackers and creators of malicious software. As part of this article, we will consider how to deal with one of the popular viral miners.
Remove XMRIG CPU Miner
Initially, the XMRIG CPU Miner program itself was and remains quite a conscientious miner, with which users produce MONERO currency, however, there is also the same mining virus that uses the power of a careless computer's computer processor for hidden mining of cryptocurrencies by third-party persons. You can deal with it by two main ways that are available for combining.Method 1: Automatic Removal
The mining viruses are very secretive and lively, therefore it is not a fact that even the anti-virus installed you can react to the infected file in time until it has been rooted in trusted system processes of Windows and the registry. In addition, often the usual removal is missing, because the virus rewrites the standard behavior of the OS. As a consequence, when checking the system files, not finding the necessary elements, the PC will try to restore them due to the fact that Mainer created such instructions in the registry, taking care of his survival and return when trying to get rid of it.
In order to remove the virus and the capabilities of its "reincarnation", use the scanners that can be used in parallel with your anti-virus software, then find the registry problems and, if any installations will refer to remote mining files, correct them. Search and remove viruses with Kaspersky Virus Removal Tool is made like this:
/
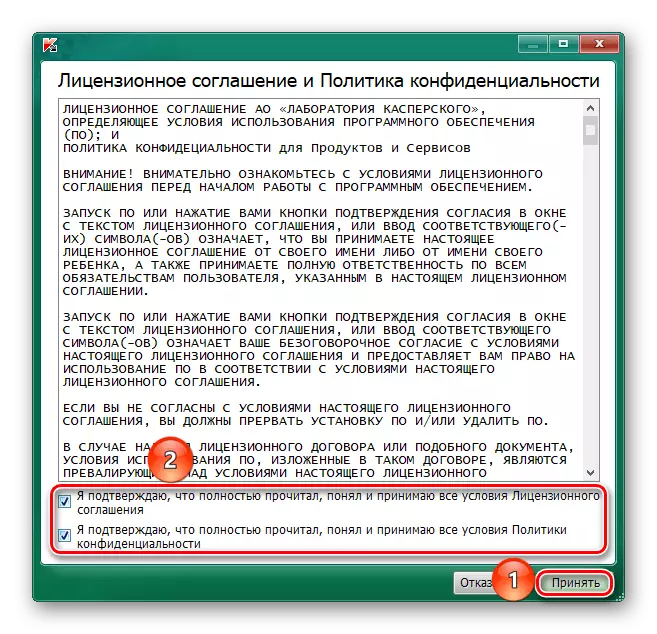
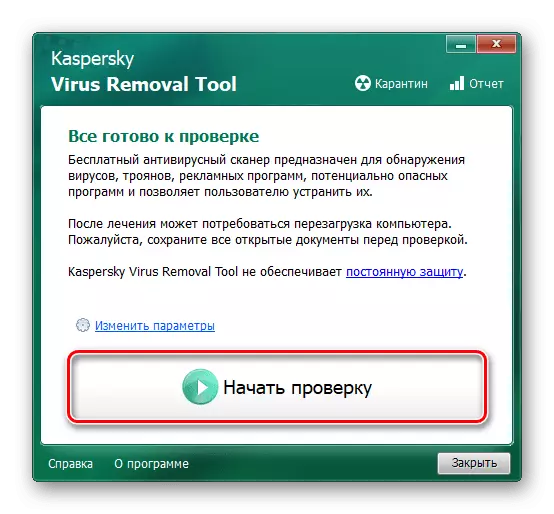
- After opening the executable file, accept the Terms of License Agreement, as well as the "Privacy Policy", clicking on the appropriate checkmarks, otherwise the scanner will not start, and then click on the "Accept" button.
- Wait for the application to initialize.
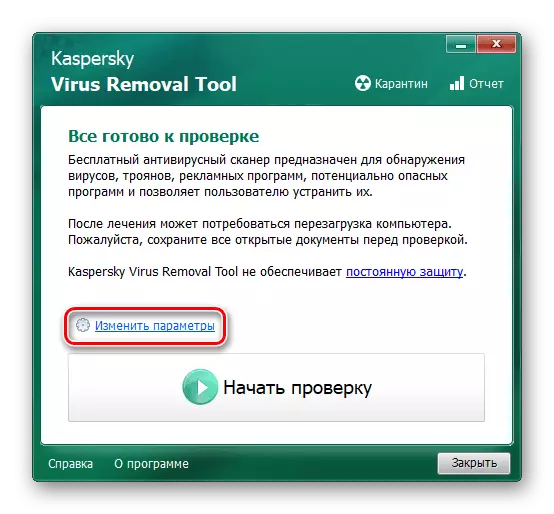
- Click on "Change Parameters" in order to expand the search area of malicious software.
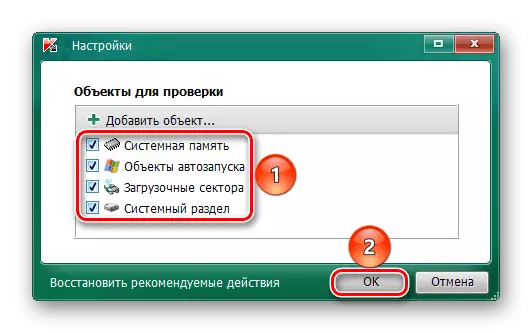
- Select all possible objects to check and click OK.
- Click the left mouse button to "start checking".
- Wait until the utility checks.
- When all threats are found, click on the scope of the action with them and select "Delete", then click "Continue".
- Wait for treatment while treatment.
- Evaluate the results of the inspection and neutralization of threats, and then complete the work with the program by clicking on "Close".
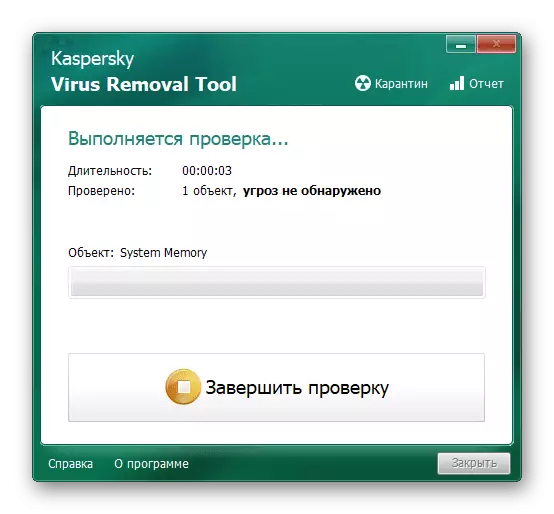
Kaspersky Virus Removal Tool is an extremely meticulous scanner, especially in cases where you need to check all the elements of the system, so the diagnosis can take about ten minutes and even more.
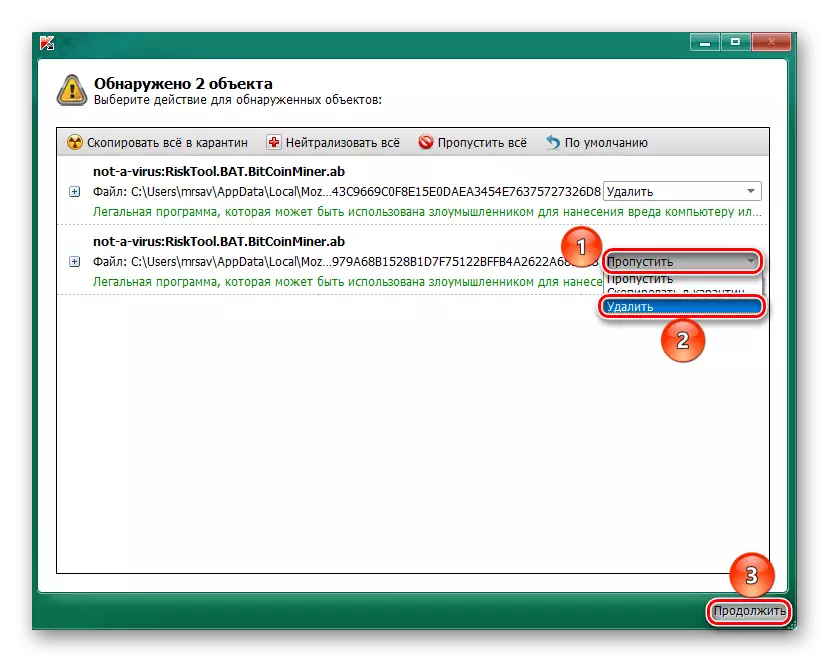
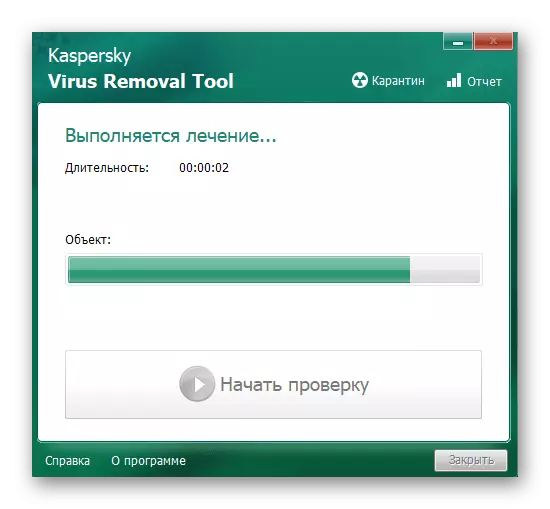
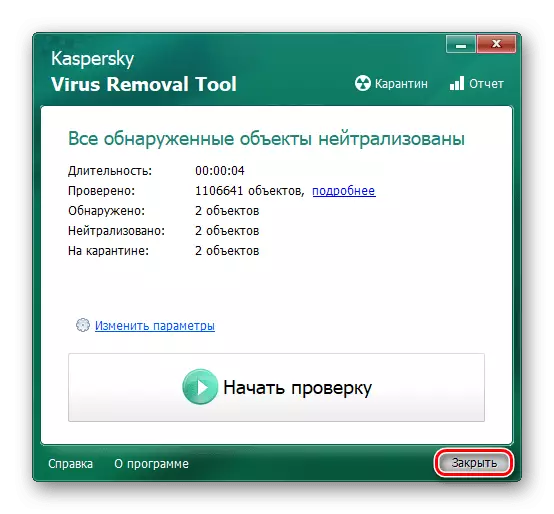
The attending utility Kaspersky Virus Removal Tool is perfectly coping with the removal of mining viruses, and the XMRIG CPU MINER is no exception, the only inconvenience can be the fact that if the infected file is able to hide well, in which case it will take several dozen minutes of your time.
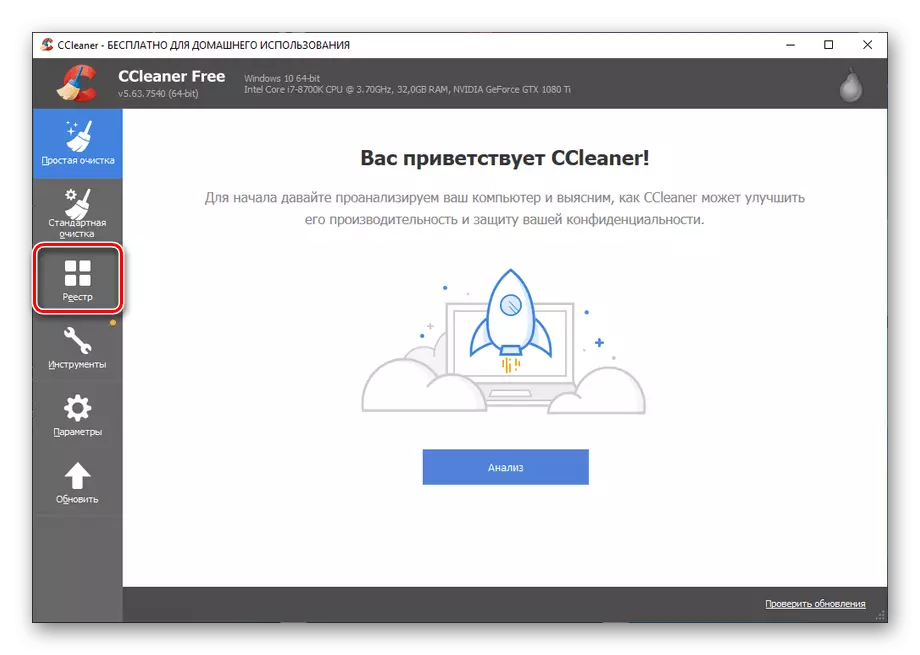
Effectively use the attending utility in combination with an optimizer in order to clear the registry OS from the remnants of malicious software and guarantee the non-return of the virus. We recommend that you use CCleaner and make such actions:
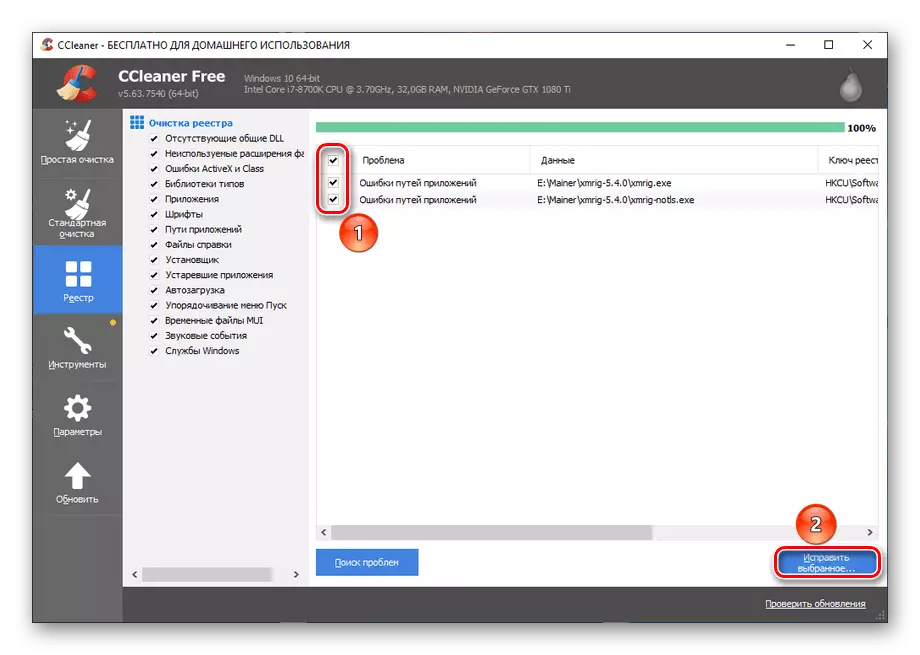
- Select the Registry section.
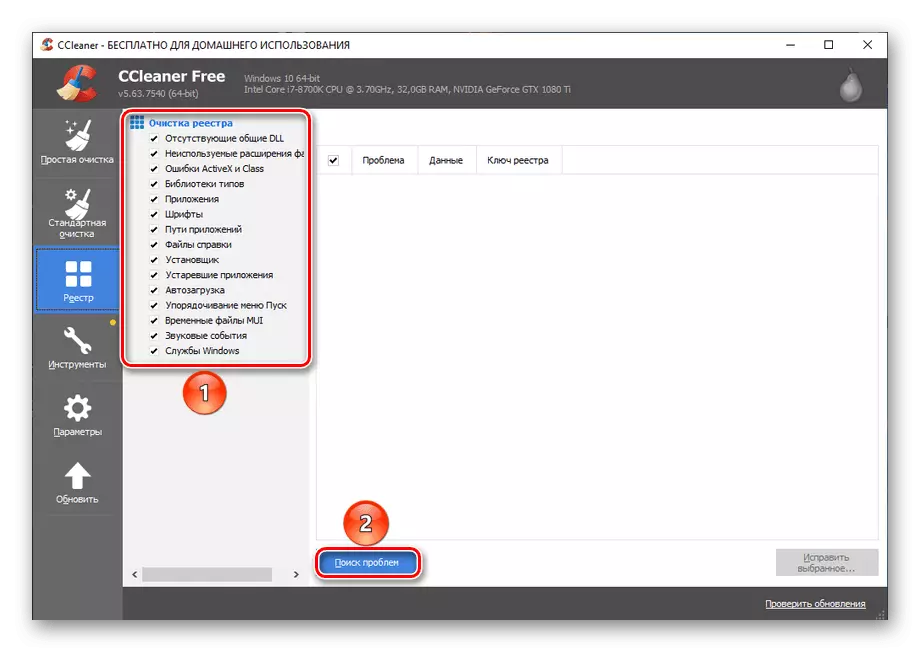
- Mark all possible troubleshooting options and click "Problem Search".
- Wait until the application is looking for failures.
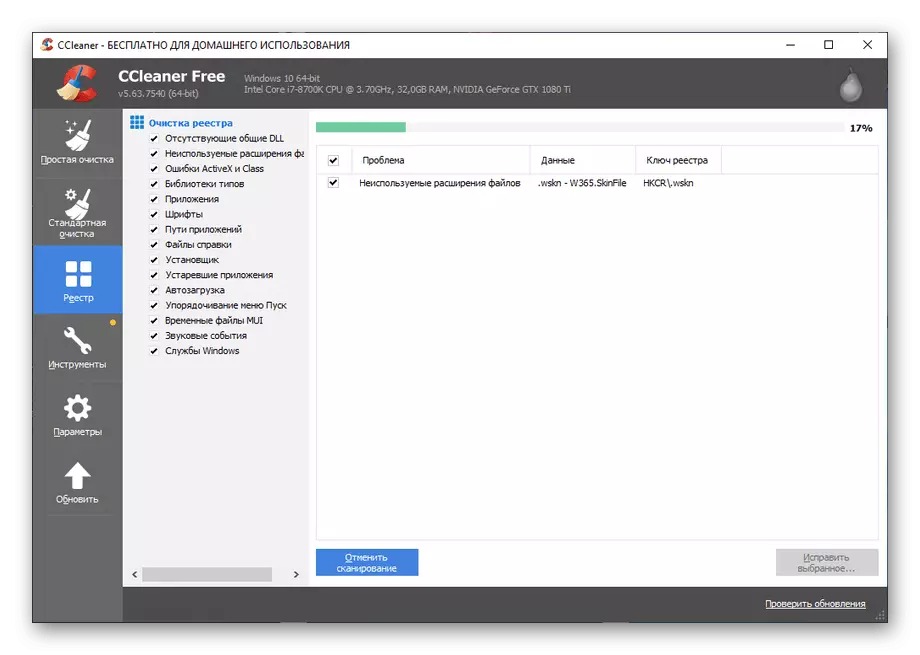
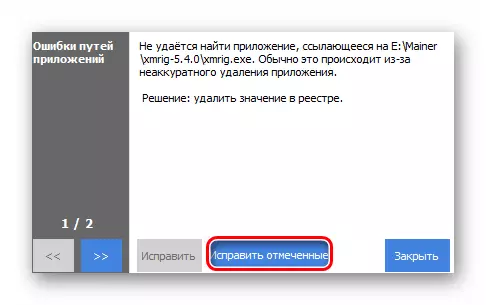
- Select all the registry problems found and click Fix Selected.
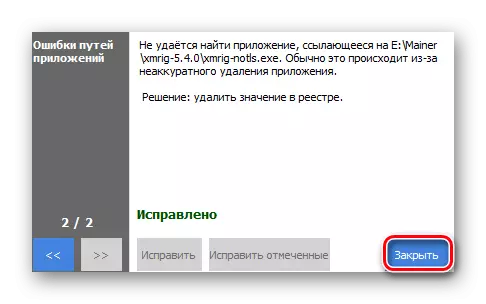
- Click on "Fix marked" to immediately deal with all found.
- Complete the work with the program by clicking on "Close".
Although it is not necessarily, but we strongly recommend reloading the computer to make the system changes to come into full force.
The use of the attending utility and an optimizer is an effective measure against all malicious software and mining viruses in particular. Thus, you clear the system and do not leave the possibility of maliciously reinstall.
Method 2: manual removal
No possibility or reluctance for any reason to use a specialized software for finding and malicious software and repairing the registry will not be an obstacle to remove the virus, although it will be somewhat more complicated. It is necessary to produce the entire procedure in manual mode in 3 consecutive stages, which will be discussed later on the example of Windows 10.
Step 1: Delete Program
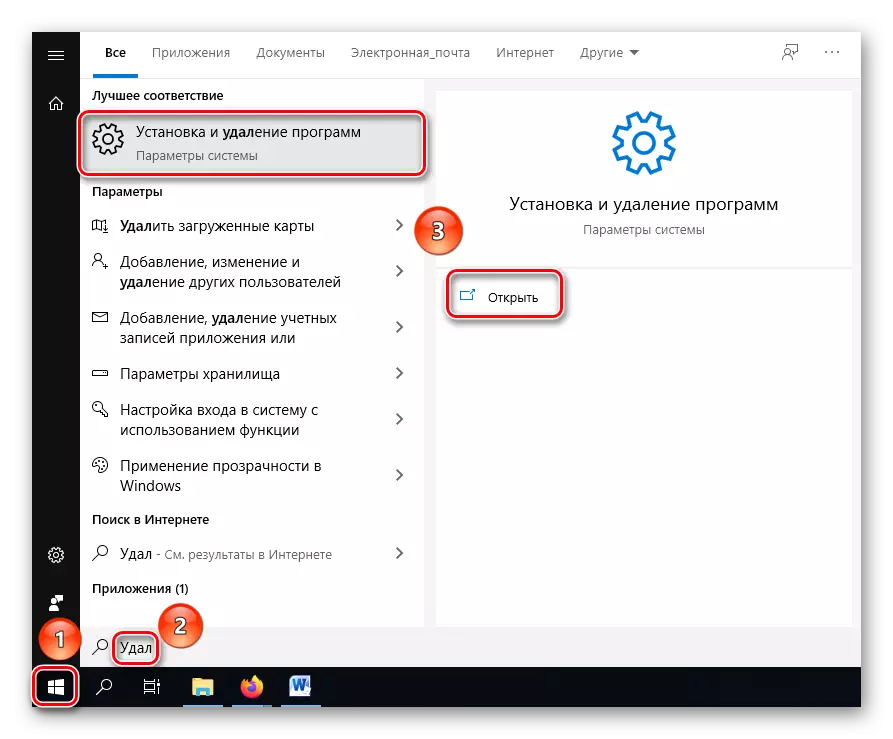
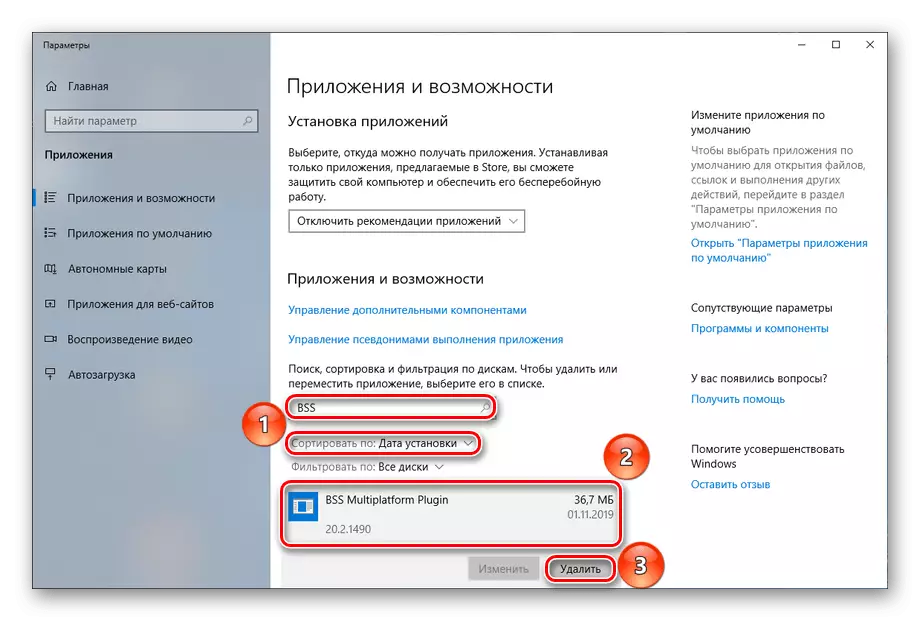
- Find the "Install and Delete Programs" through the Start menu and open it.
- In the search bar, find the application you suspect in harmfulness, or sort them all by the category "Installation Date" to find recently installed if you are not sure which program drives the system. After defining the application, delete it by clicking on the "Delete" button.
This method of removal is at least no originality, but it can work if the cause of infection has become the installation of a third-party application. At the same time, malicious software can be masked, and then they will have to go for some tricks to remove it, which is detailed in detail in the articles below.
Turning off the dangerous on the possibility of autoloading, you will prevent its return to the PC and the restoration of malicious functionality.
It is likely that you will not have any similar process after deleting the program and this action can be skipped. But if the process of the same name with the virus is still present, use the item "Open the location of the file" By clicking on the PKM on it, and manually clean the remnants of suspicious applications.
Step 3: Registry Cleaning
When the software itself and instructions for its autoload are removed, the next step will be to clean the registry from malicious elements.
From now on, the registry is completely free from the influence of the virus, and the risk of meeting it again due to the automatic recovery is eliminated.
Restoring files
The last chord in the cleaning of the OS will be restored by damaged files, because if the virus has mimicarized under the useful software and interacts with the system for a long time, then the likelihood is that it has a certain damage to Windows components. This damage can be determined and filling out by producing the following actions:
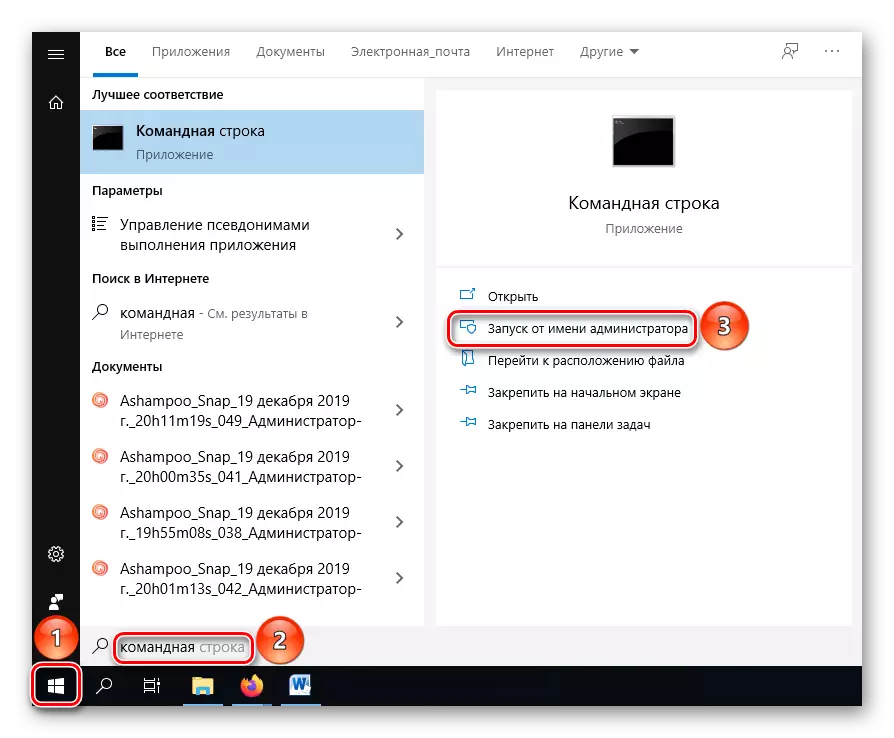
- Find and open the "Command Line" application in searching the "Start" menu, initiate the "Run from the administrator name" so that the string perceived the desired command, which may not happen in normal mode.
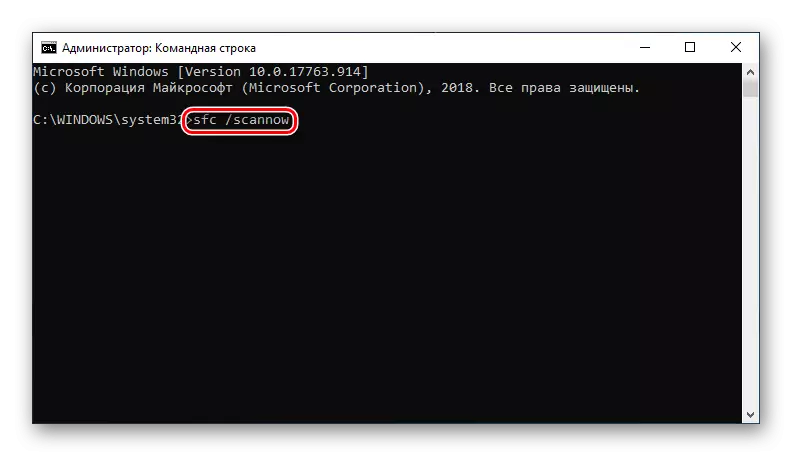
- Enter the SFC / ScanNow command, it will start scanning the system and automatically correct damaged files, which may take a decent amount of time.
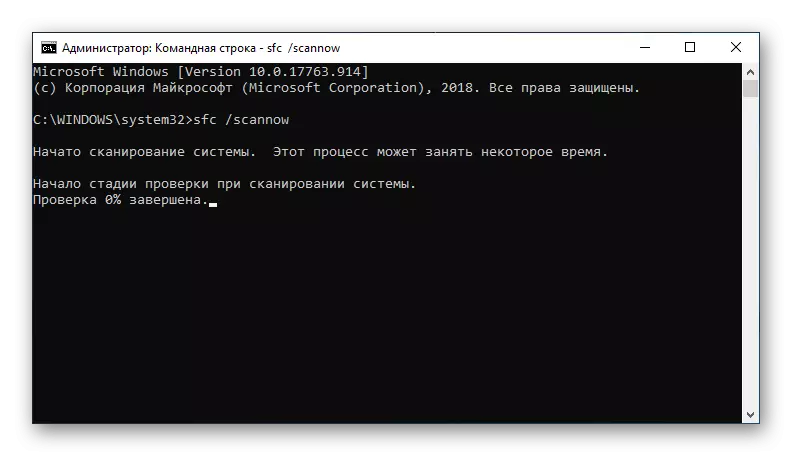
- Wait until the PC checks the system, do not expect the rapid cessation of the process.
- Browse the result of scanning and recovering files.
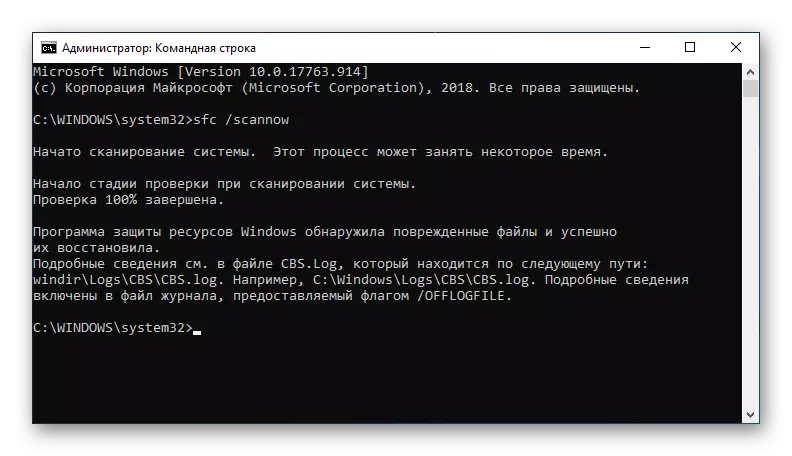
Try not to climb the left mouse button over the interface "Command Line" During check or restore files. This can lead to hanging and suspension of the executable command. If you are suspected an enlightening application, click on the button. "ENTER" In order to check the status of the executable process.
Thus, you eliminated the consequences of staying the mining virus on your computer. It remains to restart the PC and be content with the work done by hand. And you should not forget that the methods described above can be combined, first performing automatic check, and after yourself get rid of traces. In this case, you can be fully confident that malware disappeared from your computer.
In the course of the article, two integrated methods were set out how to remove XMRIG CPU Miner from your computer. If you have the ability to download and use third-party software, you will help Kaspersky Virus Removal Tool or Dr.Web Cureit!, As well as CCleaner. Otherwise, you can manually remove the virus and restore the system.
