
This material is a continuation of the article "How can hack your password" and implies that you are familiar with the material set out there or without even know all the main paths that passwords can be compromised.
Creating passwords
Today, when registering any Internet account, creating a password, you usually see the password reliability indicator. Almost everywhere it works on the basis of the assessment of the following two factors: password lengths; The presence of special characters, capital letters and numbers in the password.
Despite the fact that these are really important password stability parameters for hacking method of extinguishing, a password that seems to the system reliable, is not always that. For example, a password like "PA $$ W0RD" (and there are also special characters, and numbers), most likely, will be hacked very quickly - due to the fact that (as described in the previous article) people rarely create unique passwords (less than 50% of passwords are unique) and the specified option is greater likely to have in leaked databases available from intruders.
How to be? The optimal option is to use password generators (there is online in the form of online utilities, as well as in most password managers for a computer), creating long random passwords using special characters. In most cases, the password out of 10 or more such characters simply will not be of interest to the hacker (i.e., its software will not be configured to select such options) due to the fact that the cost of time will not pay off. The recently built-in password generator appeared in the Google Chrome browser.
In the specified method, the main disadvantage is that such passwords are difficult to remember. If there is a need to keep the password in the head, there is another option based on the fact that the password out of 10 characters containing capital letters and special characters is selected by the method of busting in thousands and more (specific numbers depend on the permissible set of characters) times simpler, than a password of 20 characters containing only lowercase Latin characters (even if the hacker knows about it).
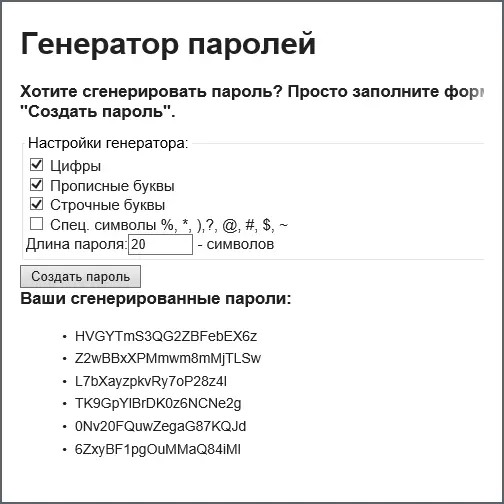
Thus, a password consisting of 3-5 simple random English words will be easily remembered and almost impossible to hack. And I wrote every word from the capital letter, we will build the number of options in the second degree. If this will be 3-5 Russian words (again random, not names and dates), written in English layout, also removes the hypothetical possibility of sophisticated methods of using dictionaries to select a password.
Definitely the right approach to the creation of passwords is probably not: in various ways there are advantages and disadvantages (related to the ability to remember it, reliability and other parameters), but the basic principles look like this:
- The password must consist of a significant number of characters. The most common restriction today is 8 characters. And this is not enough if you need a protected password.
- If possible, special characters, title and capital letters, numbers should be included in the password.
- Never include personal data on password, even recorded by seemingly "cunning" ways. No dates, names and surnames. For example, hacking a password representing any date of the modern Julian calendar from the 0th year and to today (of the form 07/18/2015 or 18072015, etc.) will take from seconds to hours (and then the clock will only succeed due to delays Between attempts for some cases).
You can check how reliable your password on the site (although the password entry on some sites, especially without HTTPS, is not the safest practice) http://rumkin.com/tools/password/passchk.php. If you do not want to check your real password, enter the same (from the same number of characters and with the same set of them) to get an idea of its reliability.
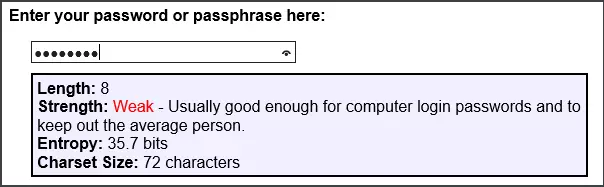
In the course of entering characters, the service calculates entropy (conditionally, the number of options for entropy of 10 bits, the number of options is 2 to the tenth degree) for a given password and provides a certificate for the reliability of various values. Passwords with entropy more than 60 are almost impossible to hack even during a focused selection.
Do not use the same passwords for different accounts.
If you have an excellent difficult password, but you use it everywhere where you can, it automatically becomes not completely reliable. Once hackers broke any of the sites, where you use a password and have access to it, to be sure, he will be immediately tested (automatically, using special software) on all the other popular e-mail, gaming, social networks, and perhaps in Online banks (ways to see whether your password is already presented at the end of the previous article).
A unique password for each account is difficult, it is inconvenient, but it is necessary if these accounts are at least some importance for you. Although, for some registrations that have no value for you (that is, you are ready to lose them and do not worry) and not containing personal information, you can not strain with unique passwords.
Two-factor authentication
Even reliable passwords do not guarantee that no one can go to your account. You can steal the password with one way or another (phishing, for example, as the most common option) or to be familiar with you.
Almost all serious online companies including Google, Yandex, Mail.Ru, Facebook, in contact, Microsoft, Dropbox, Lastpass, Steam and others with a relatively recently added the ability to enable two-factor (or two-step) authentication in accounts. And if security is important to you, I highly recommend it to include.
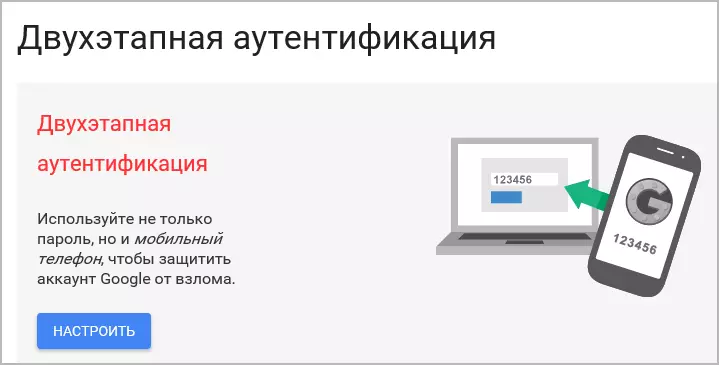
The implementation of the operation of two-factor authentication is slightly different for various services, but the basic principle is as follows:
- When entering the account with an unknown device, after entering the correct password, you are asked to undergo an additional check.
- Checking occurs using the SMS code, a special application on the smartphone, through pre-prepared printed codes, e-mail messages, a hardware key (the last option appeared at Google, this company is generally front-line in terms of two-factor authentication).
Thus, even if the attacker found out your password, he will not be able to enter your account, without having access to your devices, telephone, email.
If you are not fully understood, how two-factor authentication works, I recommend reading the article on the Internet on this topic or descriptions and guidance on the sites yourself, where it is implemented (just detailed instructions in this article will not be turned on).
Storage of passwords
Sophisticated unique passwords for each site are excellent, but how to store them? It is hardly all these passwords will be able to keep in your head. Storing saved passwords in the browser is a risky undepair: they not only become more vulnerable to unauthorized access, but simply can be lost in case of system failures and when synchronization is disabled.
The optimal solution considered password managers, in general terms, is a program that stores all your sensitive data in encrypted secure storage (both offline and online), which can be accessed using a single master password (optional, you can turn on two-factor authentication). Also, most of these programs are equipped with tools for generating and evaluating the reliability of passwords.
A couple of years ago I wrote a separate article about the best password managers (it should be rewritten, but to get an idea of what it is and what programs are popular because of article). Some prefer simple offline solutions, like Keepass or 1Password, storing all passwords on your device, others are more functional utilities, which are also synchronization features (LastPass, Dashlane).
Famous password managers are generally considered as a very safe and reliable way to store them. However, it is worth considering some details:
- To access all your passwords, you need to know only one master password.
- In the event of an online storage hacking (literally a month ago, the most popular LastPass password management service has been hacked) You will have to change all your passwords.
How else can you save your important passwords? Here are a pair of options:
- On paper in a safe, access to which you will have you and members of your family (not suitable for passwords that you want to use often).
- Offline password database (for example, KEEPASS), stored on a durable information and duplicated somewhere in case of loss.
Optimal in my opinion the combination of all of the above described is the following approach: the most important passwords (the main e-mail, with which other accounts can be restored, the bank, etc.) is stored in the head and (or) on paper in a safe place. Less important and, at the same time, often used should be entrusted with password managers.
Additional Information
I hope a combination of two articles on passwords to someone from you helped pay attention to some aspects of the security that you did not think about. Of course, I have not taken into account all possible options, but simple logic and some understanding of the principles will help independently decide how safe what you are doing at a specific point. Once again, some of the mentioned and several additional items:
- Use different passwords for different sites.
- Passwords should be difficult, you can increase the difficulty stronger, increasing the password length.
- Do not use personal data (which can be founded) when creating a password, tips to it, control questions for recovery.
- Use two-step authentication where possible.
- Find optimal way to secure password storage.
- Fancy Phishing (check the addresses of sites, encryption) and spyware. Everywhere, where they ask you to enter a password, check if you really enter it on the right site. Watch that there is no malicious software on the computer.
- If possible, do not use your passwords on other people's computers (if necessary, do it in "incognito mode" browser, and even better dial-screen keyboard), in public open Wi-Fi networks, especially in the absence of encryption https when connecting to the site .
- Perhaps it is not necessary to store the most important, indeed vital representing the value of passwords on the computer or online.
Something like this. I think I managed to raise the degree of paranoia. I understand that much of the described seems inconvenient, there may be thoughts like "Well, it will be bypass," but the only exclusiveness of laziness, when followed by simple safety rules, when storing confidential information, there may be only the absence of its importance and your willingness to That she will be the heritage of third parties.
