
There are several modifications of such viruses or trojans-extortioners (and newly appear new), but the overall essence of the work comes down to the fact that after installing your documents, images, and others on a computer, potentially encrypted with changing the expansion and deletion of original files, After that, you receive a message in the readme.txt file that all your files have been encrypted, and for their decryption you need to send a certain amount of an attacker. Note: In Windows 10 Fall Creators Update, built-in protection against encryption virusers appeared.
What to do if all important data is encrypted
For a start, some general information for encrypted with the encryption of important files on your computer. If important data on your computer has been encrypted, then first you should not panic.If you have such an opportunity, from the computer disk on which a virus encrypter appeared (Ransomware) to copy something to an external drive (USB flash drive) an example of a file with a textual request for a decoder, plus any instance of the encrypted file, and then Features, turn off the computer so that the virus can continue to encrypt the data, and perform the other actions on another computer.
The next stage - with the help of available encrypted files, find out exactly what type of virus has encrypted your data: for some of them there are decoders (some I will indicate here, some are closer to the end of the article), for some - not yet. But even in this case, you can send examples of encrypted files to anti-virus laboratories (Kaspersky, Dr. Web) to explore.
How exactly to find out? You can do this using Google, finding discussions or type encrypter to expand the file. Also began to appear services to determine the type of Ransomware.
No more Ransom
No more Ransom is an actively developing resource supported by the security developers and available in the version in Russian, aimed at combating viruses with encrypters (extortioned Trojans).

If you succeed, No More Ransom can help decrypt your documents, databases, photos and other information, download the necessary programs for decryption, as well as get information that will help avoid threats in the future.
On No More Ransom, you can try to decrypt your files and determine the type of encrypter virus as follows:
- Click "Yes" on the main page of the service https://www.nomoreransom.org/ru/index.html
- The Crypt Sheriff page opens, where you can upload examples of encrypted files with a size of no more than 1 MB (I recommend downloading not containing confidential data), as well as specify email addresses or sites to which fraudsters require redemption (or download Readme.txt file with requirement).
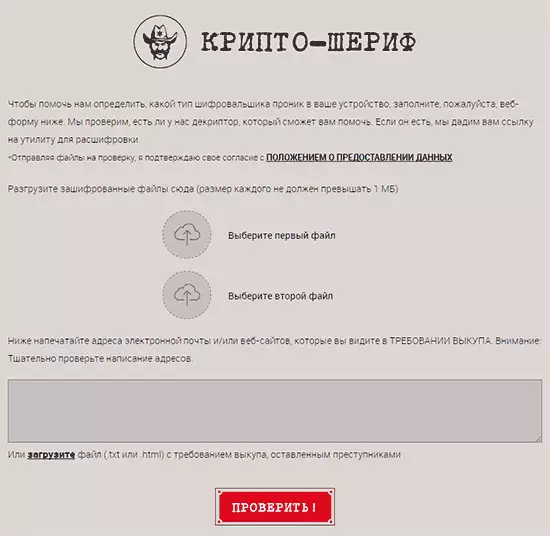
- Click the "Check" button and wait for the verification and the result.
Additionally, useful sections are available on the site:
- Deciphes - Almost all currently existing utilities for decoding encrypted files encrypted by viruses.

- Prevention of infection - information aimed primarily on novice users who can help avoid infection in the future.
- Questions and Answers - Information for those who want to better understand the work of encrypters viruses and actions in cases where you encountered the fact that the files on the computer were encrypted.
Today, no more Ransom is probably the most relevant and useful resource associated with decoding files for a Russian-language user, I recommend.
ID Ransomware.
Another such service - https://id-ransomware.malwareHuntehamware.malwareHunteham.com/ (True, I do not know how well it works for Russian-language variants of the virus, but it is worth trying to make the service example of an encrypted file and a text file with the requirement of redemption).
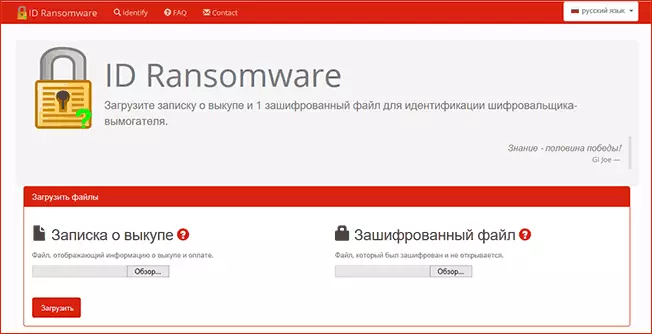
After determining the type of encrypter, if you succeed, try to find the utility to decrypt this option on requests like: Type_chifrovaster Decryptor. Such utilities are free and manufactured by antivirus developers, for example, several such utilities can be found at the Kaspersky website https://support.kaspersky.ru/viruse/UTILITY (other utilities are closer to the end of the article). And, as already mentioned, feel free to contact the developers of antiviruses on their forums or in the post office.
Unfortunately, all this does not always help and do not always have operating file decryrs. In this case, the scenarios are different: many pay intruders, encouraging them to continue this activity. Some users help programs to restore data on a computer (as the virus, making an encrypted file, removes a normal important file that theoretically can be restored).
Files on a computer are encrypted in XTBL
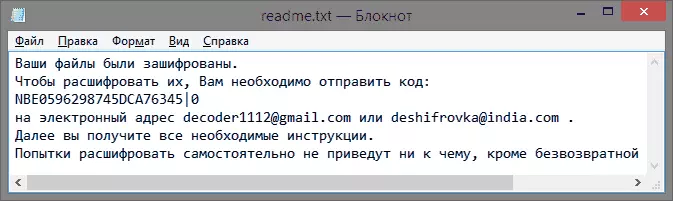
One of the latest variants of the extortion virus encrypts files by replacing them to files with the .XTBL extension and a name consisting of a random set of characters.

At the same time on the computer there is a text file readme.txt with about the following content: "Your files have been encrypted. To decipher them, you need to send the code to the email address [email protected], [email protected] or [email protected]. Next you will receive all the necessary instructions. Attempts to decipher files will independently lead to irrevocable loss of information "(mail address and text may differ).
Unfortunately, there is no way to decipher .XTBL at the moment (as soon as it appears, the instruction will be updated). Some users who have really important information on the computer reported on antivirus forums that they sent 5000 rubles from the virus authors or another required amount and received an alifranger, but it is very risky: you can get anything.
What if the files were encrypted in .xtbl? My recommendations look like this (but they differ from those that have many other thematic sites, where, for example, it is recommended to turn off the computer from the power supply immediately or remove the virus. In my opinion, it is superfluous, and at some coincidence may even be harmful, but to solve you.):
- If you know how to interrupt the encryption process by removing the appropriate tasks in the task displays, turning off the computer from the Internet (this may be a necessary encryption condition)
- Remember or write a code that attackers need to be sent to an email address (not only in the text file on the computer, just in case it is also not encrypted).
- Using Malwarebytes Antimalware, trial version of Kaspersky Internet Security or Dr.Web Cure It Remove the virus encrypting files (all listed tools are well coped with this). I advise you to take turns to use the first and second product from the list (however, if you have an antivirus installed, installing the second "top" is undesirable, as it can lead to problems in the computer.)
- Expect when a decoder from any antivirus company appears. In the forefront here Kaspersky Lab.
- You can also send an example of an encrypted file and the required code on [email protected] if you have a copy of the same file in the unencrypted form, send it too. In theory, it can accelerate the appearance of the decoder.
What should not do:
- Rename encrypted files, change the expansion and delete them if they are important to you.
This is perhaps everything I can say about encrypted files with the .XTBL extension at the moment.
Files encrypted Better_call_saul
From the last encrypter viruses - Better Call Saul (Trojan-Ransom.win32.shade), setting the .better_call_saul extension for encrypted files. How to decrypt such files - so far it is not clear. Those users who contacted the Kaspersky laboratory and Dr.Web received information that it is impossible to do this while (but still try to send - more samples of encrypted files in developers = more likely to find a method).If it turns out that you have found a method of decryption (i.e. it was somewhere laid out, and I did not rule), please share in the comments of information.
Trojan-Ransom.win32.aura and Trojan-Ransom.win32.rakhni

The next Trojan, encrypting files and establishing expansion from this list:
- .locked
- .crypto
- .kraken.
- .Aes256 (not necessarily this Troyan, there are others that establish the same expansion).
- .codercsu @ gmail_com
- .enc.
- .oshit.
- Other.
To decrypt files after the operation of the specified viruses, there is a free RakhnideCryptor utility available on the official page http://support.kaspersky.ru/viruses/disinfection/10556.

There is also a detailed instruction on the use of this utility, showing how to restore encrypted files from which I would, just in case, removed the item "Delete encrypted files after successful decoding" (although, I think, everything will be fine with the option).
If you have a DR.Web Anti-Virus license you can use the free decoding from this company on the page http://support.drweb.com/new/free_unlocker/
More options for encrypter virus
More easily, but also meet the following troyans, encryption files and requiring money for decoding. According to the above links, there are not only utilities for returning your files, but also a description of the signs that will help determine that you have this particular virus. Although in general, the optimal path: with the help of Kaspersky Anti-Virus, scan the system, find out the name of Trojan on the classification of this company, and then look for a utility by this name.- Trojan-Ransom.Win32.Rector - Free RectORDECRYPTOR utility for decoding and use manual Available here: http://support.kaspersky.ru/viruses/disinfection/4264
- Trojan-Ransom.win32.xorist is a similar Trojan, displaying a window with a request to send a paid SMS or contact an email to receive instructions for decoding. Instructions for restoring encrypted files and the XoristDecryptor utility for this is on the page http://support.kaspersky.ru/viruses/disinfection/2911
- Trojan-Ransom.win32.rannoh, Trojan-Ransom.win32.fury - RannohDecryptor utility http://support.kaspersky.ru/viruses/disinfection/8547
- Trojan.Encoder.858 (XTBL), Trojan.Encoder.741 and others with the same name (when searching through Dr.Web Anti-Virus or Cure IT utility) and different numbers - try search on the Internet named Trojan. For part of them there are decryption utilities from Dr.Web, as well, if you failed to find a utility, but there is a DR.Web license, you can use the official page http://support.drweb.com/new/free_unlocker/
- Cryptolocker - To decrypt files after working Cryptolocker, you can use the site http://decryptcryptolocker.com - after sending an example of the file, you will receive a key and utility to restore your files.
- On the site https://bitbucket.org/jadacyrus/ransomwareremovalkit/downloads Access Ransomware Removal Kit - a large archive with information on different types of encrypters and dysfolia for decoding (in English)
Well, from the latest news - Kaspersky Lab, together with law enforcement officers from the Netherlands, developed Ransomware Decryptor (http://noransom.kaspersky.com) to decipher files after CoinVault, but in our latitudes this extortion is not found.
Protection against encrypter viruses or Ransomware
As Ransomware spreads, many manufacturers of antiviruses and malware struggles began to produce their solutions to prevent encryption holders on the computer, among them you can allocate:- MalwareBytes Anti-Ransomware

- BitDefender Anti-Ransomware
- WINANTIRSOM.
But: these programs are not intended for decoding, but only to prevent encryption of important files on the computer. Yes, and in general, it seems to me that these functions must be implemented in anti-virus products, otherwise it turns out a strange situation: the user needs to keep the anti-virus on the computer, the means of fighting Adware and Malware, and now the Anti-Ransomware utility, plus, just in case Anti- Exploit.
By the way, if suddenly it turns out that you have something to add (because I can not have time to monitor what is happening with the methods of decryption), report in the comments, this information will be useful to other users who collided with the problem.
